Get Avast One for iPhone to help block hackers and malware
- Security
- Privacy
- Performance
An exploit is any attack that takes advantage of vulnerabilities in applications, networks, operating systems, or hardware. Exploits usually take the form of software or code that aims to take control of computers or steal network data. Read on to learn where exploits come from, how they work, and how an award-winning security tool can keep you safe.

Exploits are programs or code that are designed to leverage a software weakness and cause unintended effects. But to define exploits, we first need to go over security vulnerabilities (or flaws).

This Article Contains:
Software and networks come with built-in protection against hackers, sort of like locks that keep unwanted guests from sneaking inside. A vulnerability, then, is like an accidental open window that a thief can climb through. In the case of a computer or network, thieves can install malicious software through these vulnerabilities (open windows) in order to control (infect) the system for their own nefarious ends. Usually, this happens without the user’s knowledge.
Vulnerability vs. exploit — what’s the difference? As mentioned, vulnerabilities are weaknesses or security flaws in a system or network that can allow malicious actors or hackers a way in. So if a vulnerability is the open window into the system, an exploit is the rope or ladder the thief uses to reach the open window. An exploit is simply a tool created to leverage a specific vulnerability — without vulnerabilities, there’s nothing to exploit.
That doesn’t mean that all vulnerabilities can be easily exploited. Sometimes the nature of a particular vulnerability is such that hackers can’t figure out how to write code that exploits it. Returning to our open window analogy, not all open windows cater perfectly to thieves — sometimes they’re too high up to reach, or they might lead only to a locked basement. The same holds true with “open windows” that are security flaws — cybercriminals can’t always take advantage of every window.
 In the illustration above, the window on the left is locked, so there’s no vulnerability. The window on the right is open and vulnerable, but too high up to exploit. The window in the middle is open and vulnerable and, crucially, close enough to the ground to exploit.
In the illustration above, the window on the left is locked, so there’s no vulnerability. The window on the right is open and vulnerable, but too high up to exploit. The window in the middle is open and vulnerable and, crucially, close enough to the ground to exploit.
Moreover, vulnerabilities can be dangerous on their own, as they can cause system crashes or malfunctions. A vulnerability might invite DoS (denial of service) or DDoS (distributed denial of service) attacks, in which attackers can bring down a website or critical system without even using an exploit.
If a vulnerability is the open window into the system, an exploit is the rope or ladder the thief uses to reach the open window. An exploit is simply a tool created to leverage a specific vulnerability — without vulnerabilities, there’s nothing to exploit.
Vulnerabilities exist in many kinds of software, and people can also inadvertently open up more weaknesses on their own — for example, by using poor privacy settings on their social media or email accounts. (That’s why it’s important to know how to change your privacy settings on Facebook and make your Instagram account private.) Security flaws can also be found in hardware, such as the pernicious Meltdown and Spectre CPU vulnerabilities.
Although both exploits and malware can have damaging effects on a device or system, they are different. Malware refers to any type of malicious software, including viruses, ransomware, spyware, etc. A free antivirus tool is the best way to defend against all types of malware.
An exploit, in contrast, is code that allows a hacker to leverage a vulnerability — for example, they can use an exploit to gain access to a computer system and then install malware on it. Though an exploit attack can contain malware, the exploit itself is not malicious. To go back to our house-and-window example, if a vulnerability is the open window into a system, the exploit is the means by which a hacker reaches the window — and they may be carrying a piece of malicious code (malware) in their backpack.
Vulnerabilities are errors in the software development process that leave accidental holes in the software’s built-in security. Cybercriminals can exploit these errors to access the software and, by extension, your entire device. Malicious developers even create exploit kits, which are collections of exploits often bundled with other software.
Hackers can buy or rent these kits on the dark web, and then hide them on compromised websites or in advertisements. When someone visits the infected site or clicks a malicious ad, the exploit kit scans their computer for any suitable vulnerabilities. If it finds one, it uses the relevant exploit to crack it open. People can also suffer attacks from exploit kits through suspicious emails, downloading files from shady sources, or phishing scams.
Hackers can use a few different ways to launch an exploit attack. One option is when you unsuspectingly visit an unsafe website that contains an exploit kit. In such a case, the kit silently scans your device, searching for unpatched vulnerabilities and trying out various exploits to enter your machine. The exploit itself might be a piece of code or set of instructions that are targeted to one specific vulnerability, or even to several vulnerabilities together.
The exploit kit can discover a variety of info, including which operating system you have, what applications you’re running, and if you use browser plug-ins such as Java. The exploit kit sifts through everything in search of a vulnerability that it can breach. While the exploit kit is hosted online, if it breaches your device, it can deploy malware, which does infect your system.
Another way hackers can launch an exploit attack is with code that can spread over a network in search of a vulnerability, like the EternalBlue and BlueKeep vulnerabilities. These exploits don’t require any interaction with a user — in fact, you could be asleep in the other room while the exploits attack your device.
Some of the most notorious botnets, such as the Mirai botnet, spread in this way. It's an efficient way for botnet creators to grow their botnets in preparation for a distributed denial of service (DDoS) attack.
Browser applications such as Java, Adobe Flash Player, Runtime Environment, and Microsoft Silverlight are particularly vulnerable to exploits. Any outdated software or operating systems are also vulnerable. That’s because updates often include security patches that fix vulnerabilities (i.e. close the "windows").
Exploits are commonly classified as one of two types: known or unknown.
Known exploits have already been discovered by cybersecurity researchers. Whether the known exploit is due to a vulnerability in the software, OS, or even hardware, developers can code patches to plug the hole. These patches are released to users as security updates. That’s why it’s crucial to keep your devices updated.
Unknown exploits or zero-day exploits, in contrast, are created by cybercriminals as soon as they discover a vulnerability, and they use the exploit to attack victims on the same day. When a zero-day exploit attack happens, software developers and cybersecurity researchers have to scramble to figure out how the exploit works and how to patch the vulnerability.
Some exploits have led to such massive cyberattacks that they’ve become nearly household names.
EternalBlue is one of the most famous — and most damaging — exploits out there. Originally developed by the NSA, EternalBlue was stolen by the Shadow Brokers hacking group and then leaked in March 2017. Although Microsoft discovered the leak and issued a security update to patch the vulnerability, many people and organizations failed to apply the patch in time. This allowed hackers to proceed with some of the most damaging cyberattacks in history, including WannaCry and NotPetya.
WannaCry was the stuff of nightmares: a wormable attack that used the EternalBlue exploit to spread exponentially across computer networks, infecting 10,000 machines per hour in 150 countries. As ransomware, WannaCry encrypted computers, rendering them inaccessible — a huge issue for the national health services, governments, universities, and large corporations that WannaCry hit. Although WannaCry is no longer active, other exploits can still take advantage of EternalBlue to attack Windows users running outdated software — so make sure yours is updated.
Petya and its amusingly named successor, NotPetya, were ransomware strains (NotPetya also relied on the EternalBlue exploit). The Petyas caused huge damage by encrypting computers’ master file table (MFT), rendering the machines completely unusable. And while there were ransom demands made, NotPetya could not be decrypted. So even if the users and organizations paid up, they never received anything in return. Experts estimate that Petya strains of ransomware caused over $10 billion in damage as they blew through banks and other corporations.
BlueKeep is an exploitable vulnerability in Microsoft Remote Desktop Protocol (RDP) that can allow attackers to log in to a victim’s computer remotely. Microsoft raised the alarm about BlueKeep in May 2019, and issued a patch even for outdated operating systems such as Windows XP. That unusual step demonstrates the potential severity of BlueKeep: as it's another wormable exploit, many security researchers feared that BlueKeep would lead to the next devastating worldwide cyberattacks. As of this writing, BlueKeep has yet to amount to much, but it’s still important to patch your system so you won’t be caught in any future attacks.
Since exploits take advantage of security holes in software, there aren’t any typical signs you can recognize — a user has almost no way of knowing they’ve been affected until it’s too late. That’s why it’s important to always update your software and install security patches released by your software’s developer. If the developer has released a patch for a known vulnerability and you don’t install it, you’ll be leaving the window open for hackers and other malicious actors.
And while you might not notice an exploit, once malware sneaks in, you’re sure to feel the effects. Look for common signs of a malware infection, such as:
Slow performance
Frequent crashes or freezes
Unexplained changed settings
Tons of pop-ups or ads where they shouldn’t be
Loss of storage space
If you see any of these red flags, you should perform a virus scan with a reputable antivirus tool right away.
Avast One will scan your device from top to bottom to detect any malicious code that shouldn’t be there, and then remove it with a single click. Get 24/7 protection against future attacks, whether they come from exploits, unsafe websites, malicious email attachments, or anywhere else. Avast will block it all — with our completely free antivirus software.
Because most exploits are the result of failures by developers, plugging vulnerabilities in order to remove exploits is their responsibility. Developers will code and distribute fixes for all known exploits. Many cybersecurity watchdog organizations stay on the lookout for zero-day exploits as well, so that fixes can be developed for those, too.
In the meantime, if your device suffers an exploit attack that infects your machine with malicious code, make sure to remove the malware and then update your software – including installing driver updates.
To prevent hackers from using an exploit, it’s your job to keep all your software updated. That means installing software updates right away, no matter how annoying they may seem when you’re in the middle of something else. To make the process easier, try using an app that keeps all of your most popular apps updated automatically, like Avast One.
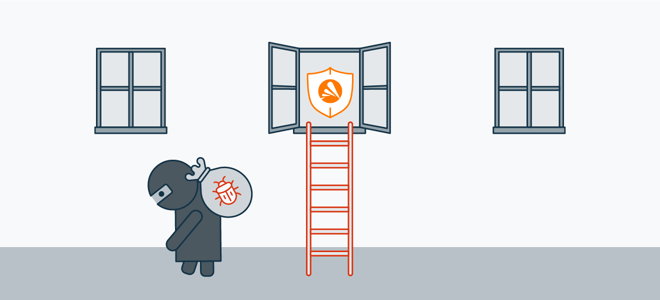 Keeping your software updated shields you against vulnerabilities, leaving hackers with nothing to exploit.
Keeping your software updated shields you against vulnerabilities, leaving hackers with nothing to exploit.
Beyond that, it’s important to always exercise common sense and practice safe computing habits. Hackers can use exploits only if they manage to access your computer. So, don’t open attachments from suspicious senders or email addresses, and don’t download files from unknown sources. And be wary of phishing attacks that attempt to steer you to unsafe websites.
Organizations and businesses should follow the best cybersecurity practices, such as conducting regular penetration tests to find vulnerabilities and protect users from data breaches and other threats.
As discussed above, the vulnerabilities or security flaws targeted by exploits are caused by developers’ mistakes. So it’s not easy to know if you may be inadvertently leaving the door open to cybercriminals. But you can add an extra gate around your system by using a robust cybersecurity tool like Avast One.
Avast blocks the abuse of exploits to keep you safe. And our firewall secures all incoming and outgoing traffic on your network. Whether it comes from exploits, phishing, infected downloads, or anywhere else, malware doesn’t stand a chance against Avast’s defenses.
Find any tiny crevices that might invite malware in — including outdated software, weak passwords, and unnecessary add-ons — and fill them using Avast One. Download it today to get top-notch security and privacy protection, all for free.
Download free Avast One to get real-time protection to help block hackers, malware, and other online threats.
Download free Avast One to get real-time protection to help block hackers, malware, and other online threats.
Install free Avast One to get real-time protection to help block hackers, malware, and other online threats.
Install free Avast One to get real-time protection to help block hackers, malware, and other online threats.
Get Avast One for iPhone to help block hackers and malware
Get Avast One for Android to help block hackers and malware