Infographic
Phish Phinder
Tell-tale signs of a (potentially) successful email phishing scam
Hackers use phishing emails to obtain your:
Usernames
Passwords
Credit card
All it takes is for you to take the bait by:
Opening an attachment
Clicking a malicious link
Entering sensitive information
Anatomy of a phishing email
Look for any of the following suspicious elements when opening your next email.
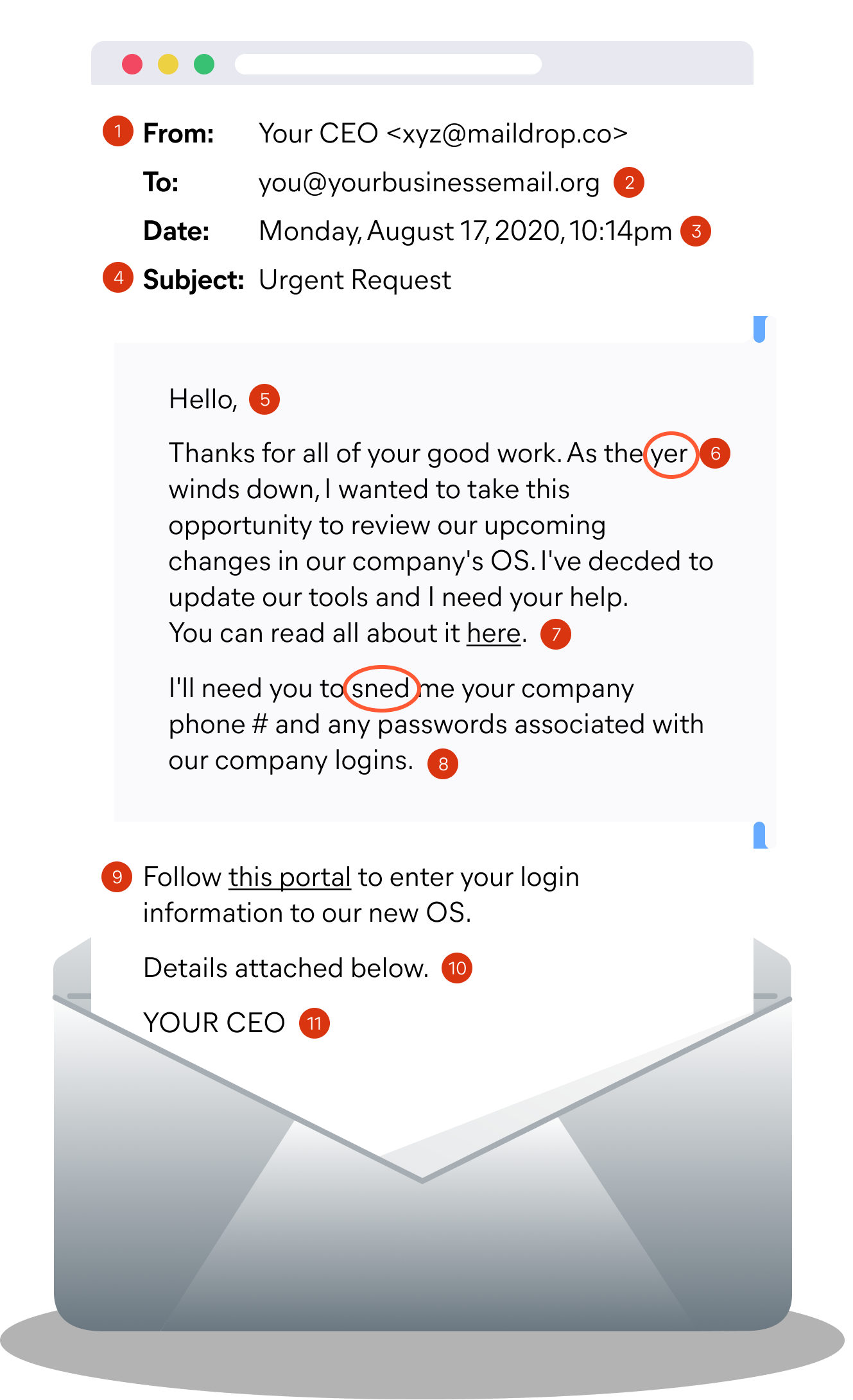
Header
- 1. Does the name match the sender? Have you received an email from this address before?
- 2. Is the email directed at undisclosed-recipients? Was it sent to several addresses?
- 3. Is this a normal time/date for this sender to have emailed you?
- 4. Is the subject something relevant to my relationship with the sender? Is the subject line requesting my immediate response or promising me a reward?
Body
- 5. Is this the senders usual greeting?
- 6. Look out for typos.
- 7. Hover over a link before clicking. Does the URL look right? Has a letter been omitted? Are they using .net when it should be .com?
- 8. If the sender is asking for private information you should immediately flag it.
Red flags
Is the content relevant to your relationship with the sender?
Is the issue really as urgent as the sender is implying?
Footer
- 9. Never offer your login information into a portal, especially if unsolicited.
- 10. Do not open unexpected attachments, especially when the file type is a .pif, .scr or .exe
- 11. Does the salutation match the sender? Is this how they usually sign off?

Don't take the bait

1 in 10 Phishing emails succeed
Remember:
- A little scrutiny goes a long way
- Be aware of the warning signs and don’t ignore them
- If it doesn’t look right, it probably isn’t
- Take a closer look before taking action
Keep your anti-spam or anti-virus software up to date.
Secure your network traffic to mitigate phishing risk at your company!