What is Cerber Ransomware?
Cerber ransomware is a type of malware (malicious software) that encrypts your files and then holds them hostage, demanding a ransom payment in exchange for returning them to you. But what makes Cerber different from some other types of ransomware? It comes down to Cerber’s business model: Cerber is ransomware-as-a-service (RaaS).
It’s hard to take two steps in today’s internet without running into the concept of software-as-a-service, or SaaS. It’s a pervasive software model in which a provider hosts the software on their own servers, then distributes it over the internet to customers. It’s no surprise that this widely successful approach has spread to the world of ransomware.
Taking cues from SaaS, Cerber’s creators license their ransomware to other cybercriminals in exchange for a percentage of the revenues their attacks generate.
How does Cerber Ransomware work?
As far as ransomware goes, Cerber is pretty cut-and-dry. Victims inadvertently install the ransomware onto their devices as a result of phishing emails, infected websites, or malvertising — malware-infected ads displayed on otherwise legitimate websites. By opening a malicious attachment, visiting an infected site, or interacting with a contaminated ad, you’ll accidentally install Cerber onto your computer.
At this point, Cerber begins encrypting your files so that you can’t open them anymore. Any files it touches are given new extensions, and without the correct decryption key, they’re locked up tight. Like other strains of ransomware, Cerber can also access files on any unmapped network shares.
How do you recognize Cerber Ransomware?
After Cerber completes its encryption processes, it’ll display a ransom note to the victim that informs them of the situation while detailing the proposed methods of payment. Here’s an example of how that might look:
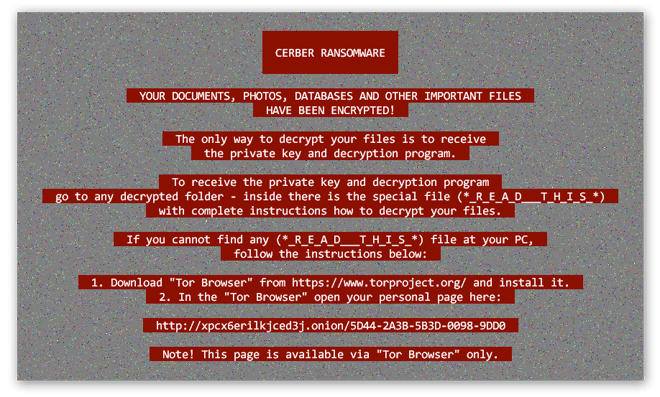
Cerber also drops a series of additional ransom notes, including an audio file that addresses the victim aloud, on victims’ desktops as well as inside any encrypted folder. The ransomware instructs victims to pay the ransom in bitcoin via the encrypted Tor Browser. In many Cerber iterations, the amount increases over time. The longer victims wait, the more they’re asked to fork over.
How to remove Cerber Ransomware?
If you’ve found yourself facing a Cerber infection, removing the malicious code isn’t going to be a big deal. Sadly, that’s not going to fix the more serious issue: decrypting your files and restoring your access to them. Still, it’s best to remove Cerber and other ransomware as soon as possible so as to prevent additional files from becoming encrypted. Here’s how:
-
Restart your computer in Safe Mode with Networking. This allows you to connect to the internet while also limiting your computer’s functionality to just the basics.
-
Once it boots up, open your preferred antivirus program. It’ll scan your computer for malware, including Cerber, then scrub it clean. If you don’t yet have one, download Avast One and let it get to work posthaste.
Again, removing ransomware like Cerber is not a cure-all. After the ransomware disappears, you’ll still be sitting on a pile of encrypted files. It’s understandable if, at this point, you’re thinking that the best path forward from here is to pay up, but this is a bad idea in more ways than one. Never pay a ransom for your own files.
Firstly, there’s no guarantee that the attacker is going to follow through on their end of the deal. Once you’ve paid, there’s nothing stopping them from turning around and disappearing. Some strains of ransomware, like Petya, use encryption methods that can’t be reversed, no matter what.
And secondly, if you concede to a cybercriminal’s demands, you’re sending the message that ransomware is a lucrative technique. If you refuse to pay, you can help dissuade attackers from using ransomware against others.
Ransomware is only a threat if the files on your computer are the only copies you have. You can easily sidestep the entire situation by performing regular backups of your files.
How to decrypt Cerber Ransomware?
If Cerber’s already infected your files, and if you haven’t made any recent backups, you’ll need another way to get your data back. While many other forms of ransomware have been decrypted — with decryptor tools available online for free — there is currently no Cerber ransomware decryptor. Without a backup, you’ll need to wait until cybersecurity researchers crack Cerber’s encryption algorithms and release a decryption tool. Don’t delete your encrypted files!
And one more time: Never pay the ransom, because there’s no guarantee that you’ll get what you’re paying for.
How to prevent a Cerber Ransomware attack?
The best defense against ransomware is prevention, because once your files are encrypted, it’s often too late to get them back. Practice the following anti-ransomware tips to keep your important data safe from cyberattackers and their malware.
-
 Never download attachments from unknown senders. Embedding malware into a seemingly-innocuous attachment is a cybercriminal’s favorite trick. Instead, report and delete any phishing emails you receive. When it comes to email attachments, only open things you are expecting to receive from people you trust.
Never download attachments from unknown senders. Embedding malware into a seemingly-innocuous attachment is a cybercriminal’s favorite trick. Instead, report and delete any phishing emails you receive. When it comes to email attachments, only open things you are expecting to receive from people you trust.
-
 Related: don’t click unknown links. The same applies here as above: if you receive an email from an untrusted sender, don’t click anything in it. Be a link skeptic everywhere you go — on forums and message boards, in comment sections, on social media, and even in messaging apps and SMS. Cybercriminals can use malicious links to send you to infected websites that perform “drive-by downloads” of malware onto your device when you visit them.
Related: don’t click unknown links. The same applies here as above: if you receive an email from an untrusted sender, don’t click anything in it. Be a link skeptic everywhere you go — on forums and message boards, in comment sections, on social media, and even in messaging apps and SMS. Cybercriminals can use malicious links to send you to infected websites that perform “drive-by downloads” of malware onto your device when you visit them.
-
 Ignore internet ads. Some ads contain hidden malware that installs itself onto your device when you click. But either way, internet ads are annoying, so leave them alone or get an ad-blocker.
Ignore internet ads. Some ads contain hidden malware that installs itself onto your device when you click. But either way, internet ads are annoying, so leave them alone or get an ad-blocker.
-
 Back up your files regularly. Ransomware loses its power if you have perfect copies of all your files stored safely away. With regular backups, you’re always prepared to recover your data in the event of a ransomware attack. If you use an external drive, be sure to disconnect it after the backup is complete — otherwise, Cerber will encrypt your backup files as well.
Back up your files regularly. Ransomware loses its power if you have perfect copies of all your files stored safely away. With regular backups, you’re always prepared to recover your data in the event of a ransomware attack. If you use an external drive, be sure to disconnect it after the backup is complete — otherwise, Cerber will encrypt your backup files as well.
-
 Always use current software. Whenever you’re prompted to update your OS or other software, do it ASAP. Software updates often patch critical vulnerabilities that cybercriminals can exploit to get their malware onto your computer.
Always use current software. Whenever you’re prompted to update your OS or other software, do it ASAP. Software updates often patch critical vulnerabilities that cybercriminals can exploit to get their malware onto your computer.
-
 Install an anti-ransomware tool. Any antivirus software worth using will automatically detect and block malware, including ransomware, at the slightest hint of trouble. Even if you accidentally download an infected attachment or visit a malicious website, you’ll still be protected.
Install an anti-ransomware tool. Any antivirus software worth using will automatically detect and block malware, including ransomware, at the slightest hint of trouble. Even if you accidentally download an infected attachment or visit a malicious website, you’ll still be protected.
Why is Cerber so popular?
Cerber’s mercenarial nature has popularized it to the extent that, at one point, it was one of the most active ransomware strains. For both its developers as well as anyone using it, the benefits of this arrangement are easy to appreciate.
Attackers wishing to carry out a ransomware campaign would previously need to develop and code their own ransomware — no simple task. But with a readymade ransomware suite all packaged up and ready to go, cybercriminals can sidestep this former barrier to entry. Why put in all the time and effort to develop your own ransomware when you can rent one instead?
Meanwhile, Cerber’s developers are freed from the burden of having to plan and execute their attacks. No contact information to harvest, no phishing emails to create, no financial details to worry about. With Cerber offered as RaaS, all they need to do is sit back and collect. The ease of this arrangement is all the more reason why you should take extra steps to protect yourself.
Protect against ransomware with Avast
Cerber and other ransomware strains are showing no signs of slowing down, and with the RaaS model, the door is wide open to more and more attacks. Arm yourself with the comprehensive cybersecurity protection of Avast One. Our anti-malware suite keeps you protected on all fronts, leaving no entry points for sneaky ransomware attacks. Join over 400 million users around the world in choosing an industry-leading antivirus.















