Can ransomware be removed?
Android ransomware is trickier to deal with than most other types of malware because removal often won’t fix the problem. This is due to how ransomware works: in many cases, it uses encryption to hold your files or device hostage. You can’t reverse the encryption without a special decryption key. Even if you successfully remove the ransomware, the encryption remains behind, rendering your files or device inaccessible.
The majority of ransomware falls into the “crypto” variety, so dubbed because it targets and encrypts individual files and folders. While removing crypto ransomware (or “filecoders”) will prevent it from doing any further damage, it’s not going to reverse the encryption that’s already taken place. Most crypto ransomware targets PCs, and there aren’t many out there currently geared towards mobile devices.
On a Pixel, Samsung phone, or other Android device, you’re most likely to encounter a type of ransomware known as a “screenlocker,” or “locker,” which as you might guess, traps your whole phone behind a ransom note. The good news is that these can be removed, and your device restored, much more readily than with filecoders. Later in this piece, we provide you with several detailed guides for Android ransomware removal.
Lots of ransomware removes itself after its work is complete, in order to prevent cybersecurity researchers from studying it and cracking its encryption algorithms. If not, an anti-malware tool for Android will usually be strong enough to scrub the ransomware from your device. Though unfortunately, it can’t undo the encryption once it’s already taken place.
Focus on prevention
With the dangers as potent as they are, preventing ransomware is the only way to keep your files safe. If you wait until you’ve been infected, it may already be too late to save your data. Keep thorough backups of all your important info on either a cloud service or a disconnected external storage device. This way, if you do get infected, you can easily restore your device back to normal.
Avast One regularly scans your device to detect and block any malicious apps, including known ransomware carriers. Stop malware before it even reaches your device with preemptive protection against infected links and vulnerable Wi-Fi networks. Our mobile security solution is powered by the same AI-based global threat intelligence network as our award-winning PC and Mac tools. Install Avast to protect yourself against ransomware.
Already dealing with an infection? Follow these three steps for Android ransomware removal.
1. Immediately isolate infected devices
If your Android device has been infected with ransomware, your first move must be to immediately quarantine it. Don’t use it on your home Wi-Fi network, and don’t connect it to any other devices. If you do, the ransomware may spread. Disconnect infected devices and isolate them to reduce the risk of further infections.
2. Find out which type of ransomware you have
With the infected Android device in isolation, it’s time to figure out what sort of ransomware you’re dealing with.
-
Crypto ransomware: More prevalent on PC than mobile, this type of ransomware encrypts your files, then demands a ransom payment in exchange for a promised decryption key — which may or may not actually exist.
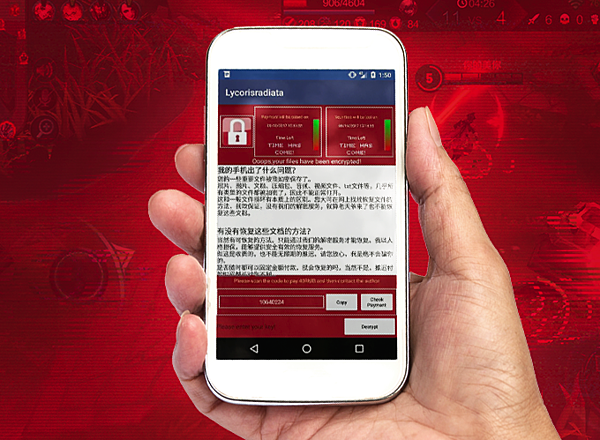
-
Locker ransomware: Often called “screenlockers,” these are the most prevalent type of ransomware for mobile. Rather than encrypt your files, a screenlocker kicks you out of your device entirely. While they’re inconvenient, screenlockers are usually easier to remove than encryption ransomware.

-
Scareware: This type of malware manipulates victims into paying for unnecessary (and often useless) software. Scareware will attempt to convince you that your Android device has been infected with a virus, and then prompt you to buy an antivirus solution that can solve all your problems. The con is that the software you’re paying for is useless, and may even be malware itself. Some scareware functions as ransomware, but usually, it’s an empty threat. That's why it's so important to use a reputable virus cleaner from a company you trust.
-
Doxxing: This isn’t malware, but there’s often a ransom involved, so it’s worth quickly mentioning here. Doxxing is digital blackmail — the threat of releasing personal or private information unless the victim pays a ransom.
All devices — PC, Mac, Android, and even iOS — have been targeted with at least one of the above types of ransomware. Today’s cybercrime landscape is broad and flexible, providing attackers with a wide range of options when it comes to extorting their victims.
Screenlockers make up the majority of Android ransomware. For example, Cyber Police — often wrongly termed the “Cyber Police virus” for Android or something along those lines — is a screenlocker Trojan that infects devices when victims click on malicious ads. Cyber Police can only infect devices running Android versions 4.0.3 to 4.4.4, so if you haven’t updated your software in a while, you may want to do so now. The Article 161 or “Koler” screenlocker is another example of this type.
How to identify your ransomware
To find out what type of ransomware has hit your phone, head to Europol’s No More Ransom hub. The Crypto Sheriff service can help identify the strain of ransomware that you have. Once you’ve figured it out, you’ll find detailed guides on what to do next.
If that’s not helpful, cybersecurity forms like those at Bleeping Computer are a good next step. The communities at these forums often help in identifying PC ransomware by looking at the extensions on the encrypted files.
3. Remove the ransomware
Once you’ve identified the type of infection you’re dealing with, it’s time to learn how to remove ransomware from Android:
Option A: The ransomware deletes itself
As mentioned above, lots of ransomware deletes itself after locking a device or the files on it. This is to prevent cybersecurity experts from studying the ransomware and potentially cracking its encryption algorithms. If the strain on your Android deletes itself automatically, you don’t need to do anything further to remove it (your files will remain encrypted, though).
Option B: Use Avast One to remove the ransomware
Avast One will purge a wide range of malware from your Android device, including many strains of ransomware. Simply fire it up and let it scan your device to remove the threat. Avast will also detect and block ransomware before it can infect your device.
Option C: Remove the ransomware manually
If you’ve got both the time and desire, it’s never a bad idea to attempt DIY methods before paying someone else to help you. Follow the steps below to try and remove the Android ransomware on your own. You’ll be restarting your device in Safe Mode, which prevents all third-party apps from running — ideally including the ransomware.
Step 1: Restart your phone in Safe Mode
This procedure may differ slightly depending on your device and Android version, but most devices will allow you reboot directly into Safe Mode.
Try holding down the Power button for a few seconds, as though you wanted to turn your phone off.
 Long-press the Power off option, then tap OK.
Long-press the Power off option, then tap OK.
 Your phone will now reboot in Safe Mode — you’ll know because your home screen should display the phrase “Safe Mode.”
Your phone will now reboot in Safe Mode — you’ll know because your home screen should display the phrase “Safe Mode.”
 Now, let’s hunt for your malware.
Now, let’s hunt for your malware.
Step 2: Check your apps
Navigate to Settings > Apps and check for any programs that don’t belong. If you see something that you don’t recall installing yourself, that’s a big red flag. Start with your most recently installed apps, as those are the most likely to be responsible for your ransomware problem, and work backwards through time.
Again, depending on your device and Android version, this process may differ slightly for you.

Step 3: Uninstall the malicious apps
When you find an app that doesn’t belong, uninstall it! Tap the app, then tap Uninstall.
 Some ransomware will give itself administrative privileges over your device, and as a result, it can deactivate its own Uninstall button. Here’s how to get around that:
Some ransomware will give itself administrative privileges over your device, and as a result, it can deactivate its own Uninstall button. Here’s how to get around that:
Step 4: Prevent unwanted apps from being device administrators
Head to your phone’s security settings and look for a list of apps with administrative privileges. Your path will likely look something like this: Settings > Security > Device Administrators. If you see any unwanted apps on this list, remove their privileges by unchecking their respective boxes and selecting Deactivate this device administrator.
 Head back to your list of apps from Step 3, and you should be able to uninstall that malicious app.
Head back to your list of apps from Step 3, and you should be able to uninstall that malicious app.
As a final measure, pop over to your Downloads folder and delete the app’s .apk installation file, if you see one.
You may now restart your phone in normal operations mode, though if any of your files were encrypted by the ransomware, they’ll still be encrypted now. If you were infected with screenlocker malware, once you remove it with the above steps and reboot, your device should be good as new.
Recover your encrypted files
If a filecoder has gotten its claws on your phone, removing it won’t decrypt your files. You’ll need to either decrypt them, or better yet, restore all your files from a recent backup. But since most Android ransomware is of the screenlocker variety, file restoration likely won’t be an issue for you.
However, if you do have a bunch of encrypted files on your hands, read on to learn how you can recover them without paying a ransom fee.
A. Restore from a backup
You can both remove ransomware from your Android phone and also restore your encrypted files by performing a factory reset if your files are safely saved in a backup. A factory reset will wipe everything on your phone — all your apps, files, and settings — then allow you to import everything back from a recent backup.
This is one big reason why it’s so important to perform regular backups on all your devices. If you’ve got an unencrypted copy of all your important files, even the most thorough filecoder won’t pose any threat. If you haven’t been backing up your system, this method won’t be of any use to you, and you probably don’t want to delete everything on your phone.
Step 1: Perform a Factory Data Reset
Head through your Settings to Backup & Reset > Factory Data Reset.
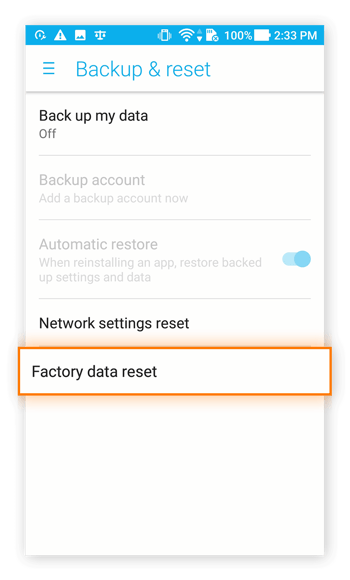
Tap Reset device to get started.
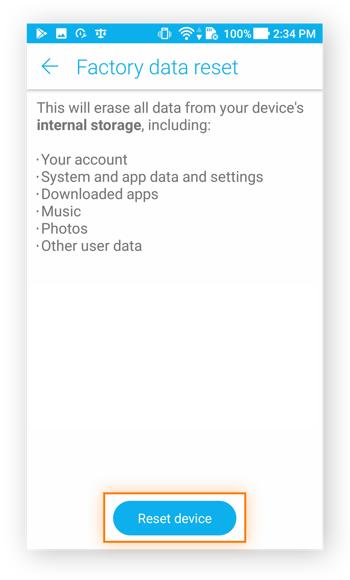
Step 2: Enter your PIN
Confirm the reset with your PIN, then tap Erase everything.
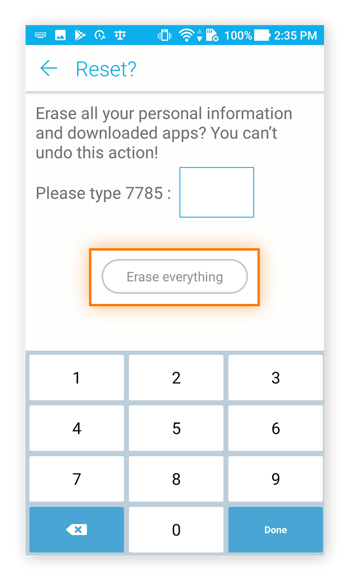
Step 3: Reboot and restore
Your phone will reboot and take you through the initial startup procedures.
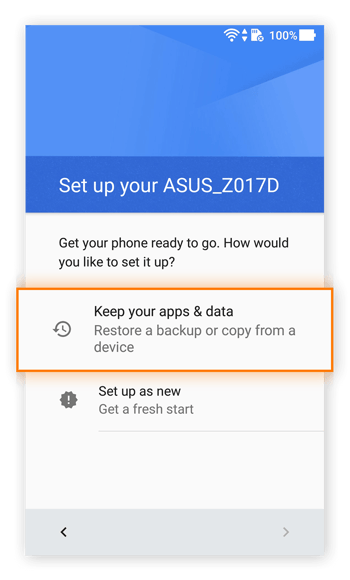
 Soon, you’ll be able to restore all your old files from the backup you hopefully created not too long ago, but before downloading the ransomware. Choose Keep your apps & data.
Soon, you’ll be able to restore all your old files from the backup you hopefully created not too long ago, but before downloading the ransomware. Choose Keep your apps & data.
B. Use decryption tools
After identifying the type of ransomware on your phone, you may be able to find decryption keys for it. If and when cybersecurity researchers crack a filecoder’s encryption algorithms, they’ll release the decryption keys to the public for free.
Most current ransomware hasn’t yet been decrypted, as once a decryption key is obtained, the ransomware ceases to pose a threat. It’s not easy to find Android decryptors online — even our own list of decryptors is currently limited to PC solutions.
If you don’t have a backup handy, you’ll need to sit tight and wait for an intrepid researcher to crack the ransomware that’s got your files locked up.
C. Don't negotiate
Ransomware is incredibly frustrating for its victims, and we sympathize with anyone who’s been forcibly deprived of their valuable files. The temptation to “just pay the ransom and get it over with” is strong, and we understand these feelings, but it’s critical that you resist. Do not negotiate with cybercriminals, and never pay their ransom demands.
If you decide to pay the ransom, you’re directly funding future criminal activities. You’re also sending the message that ransomware is an effective cybercrime tool, which can encourage cybercriminals to attack additional victims. Plus, payment is not a guarantee that you’ll get your files back, or that the ransomware will be removed.
It’s never a good idea to pay.
How does ransomware take hold of an Android device?
Many strains of PC ransomware infiltrate the computers of their victims through exploiting vulnerabilities in older operating systems. Most Android ransomware, on the other hand, needs you to handle the installation. Cybercriminals will trick victims into installing their ransomware through phishing emails, social engineering tricks, and malvertising campaigns.
Cybercriminals love to dress their ransomware up as seemingly-innocuous apps. This is exactly what happened in a 2017 mobile ransomware attack in China with a type of Android crypto ransomware disguised as a gaming app. Once you download the app and grant it the permissions it requests, the ransomware reveals its true nature. You’ll be locked out of your Android with only a ransom note to keep you company. Ransomware can also access your device through spoofed system or software update requests.
What the experts say
“The threat actors responsible for this malware generally rely on spreading through the use of third party app stores, game cheats, and adult content applications. A common infection technique is to lure users through popular internet themes and topics – we strongly recommend that users avoid attempting to download game hacks and mods and ensure that they use reputable websites and official app stores.”
Ondřej David, Malware Analysis Team Lead & Jakub Vávra, Threat Operations Analyst
Avast Threat Labs
How will I know if my phone has been infected?
All this talk about ransomware on Android devices, but what exactly does an infection look like? Find out how to check for ransomware on your phone by looking out for these two telltale signs:
-
You’re locked out: Screenlocker ransomware works by preventing you from accessing your device. Instead of your familiar lockscreen, you’ll instead see a notification alerting you that your phone has been rendered inaccessible. These apps don’t encrypt your files, but they do make your phone essentially useless.
-
You’re getting ransom notes: What’s ransomware without a ransom note? Many strains of ransomware have their own signature ransom note, a unique calling card that lets victims know three crucial bits of information:
-
Either your device is locked (screenlocker) or your files are encrypted (crypto ransomware).
-
The amount of money demanded as ransom.
-
How victims can pay — often using cryptocurrency and the Tor browser to make the payment.
Cybercriminals want you to know that you’ve been infected, and they want you to feel pressured to pay — so they’ll make it very obvious by shoving their ransom notes in your face with pop-ups.
Can Android tablets be affected, too?
Android tablets are just as vulnerable to ransomware as Android phones. For example, Cyber Police appears on tablets as well as on phones — in fact, it’s one of the most widespread strains of Android tablet ransomware out there.
Since the underlying operating system is the same, the ransomware removal techniques we’ve outlined here will work on your tablet just as effectively as they do on a phone. If your mobile security app isn’t able to quarantine and remove the ransomware, and if you can’t access Safe Mode, consult a cybersecurity expert for additional help.
Defense is the best strategy
By now, it should be clear how unpleasant it will be if your device gets infected with ransomware. That’s why the single best anti-ransomware tactic is actually prevention rather than removal. Avast One works 24/7 to keep malware off your Android mobile or tablet with thorough scans of your device and apps as well as web links and Wi-Fi networks.
If you’re not performing regular backups of your device, now’s the time to start. Many Android phones provide an option to handle this automatically. With a strong mobile security tool and a recent backup of your system and files, you’ll have nothing to fear.





 Long-press the Power off option, then tap OK.
Long-press the Power off option, then tap OK. Your phone will now reboot in Safe Mode — you’ll know because your home screen should display the phrase “Safe Mode.”
Your phone will now reboot in Safe Mode — you’ll know because your home screen should display the phrase “Safe Mode.” Now, let’s hunt for your malware.
Now, let’s hunt for your malware.
 Some ransomware will give itself administrative privileges over your device, and as a result, it can deactivate its own Uninstall button. Here’s how to get around that:
Some ransomware will give itself administrative privileges over your device, and as a result, it can deactivate its own Uninstall button. Here’s how to get around that: Head back to your list of apps from Step 3, and you should be able to uninstall that malicious app.
Head back to your list of apps from Step 3, and you should be able to uninstall that malicious app.


 Soon, you’ll be able to restore all your old files from the backup you hopefully created not too long ago, but before downloading the ransomware. Choose Keep your apps & data.
Soon, you’ll be able to restore all your old files from the backup you hopefully created not too long ago, but before downloading the ransomware. Choose Keep your apps & data.











