What is CryptoLocker ransomware and where does it come from?
CryptoLocker ransomware is a type of malware that encrypts files on Windows computers, then demands a ransom payment in exchange for the decryption key. It first emerged in September 2013 in a sustained attack that lasted until May of the following year. CryptoLocker fooled targets into downloading malicious attachments sent via emails. Once opened, these Trojan horse attachments would execute the malware hidden inside.
Was CryptoLocker a virus? Not quite. Unlike viruses and worms, CryptoLocker couldn’t make copies of itself. So how did CryptoLocker spread? To help it infect additional victims, the cybercriminals behind it made use of the now-notorious Gameover ZeuS botnet. This was a network of malware-infected computers that could be controlled remotely by the botnet’s operator, without the knowledge or consent of their owners. In other words, it was a readymade audience for a massive CryptoLocker ransomware infection.
In mid-2014, an international task force known as Operation Tovar finally succeeded in taking down Gameover ZeuS. As a result, CryptoLocker’s decryption keys were made available online for free. Though it’s difficult to pin down an exact amount, the masterminds behind CryptoLocker had successfully extracted millions of dollars in bitcoin from victims by then. Its considerable success has inspired numerous other cybercriminals to develop “clones” and derivative ransomware strains — some of which haven’t yet been cracked — that are either based on the original CryptoLocker model or simply borrow elements of its name.
How does CryptoLocker ransomware work?
CryptoLocker uses an asymmetric encryption method that makes it difficult to crack. This two-key system uses one public key for encryption and one private key for decryption, each linked to the other.
 The sender encrypts a file with the public key, and the recipient decrypts it with their private key.
The sender encrypts a file with the public key, and the recipient decrypts it with their private key.
When asymmetric encryption is used for above-board purposes, such as transmitting sensitive information, the receiver will give the public key to the sender so they can encrypt the data, but keep the private key to themselves. With ransomware like CryptoLocker, the operators hold onto both keys, including the private key that you need to decrypt your files.
Once it’s on your computer, CryptoLocker behaves much like most contemporary ransomware. It encrypts your files, then displays a ransom note informing you that you’ll need to pay a ransom fee in order to recover your files.
When executed, CryptoLocker installs itself within the user’s profile, then begins scanning the computer, any connected devices, and any other devices on its network for files and folders to encrypt. The encryption process can take hours, giving CryptoLocker a bit of an “incubation period” before the victim’s computer begins displaying symptoms.
How to recognize CryptoLocker ransomware?
As soon as the encryption process is complete, CryptoLocker makes its presence known with a ransom note.
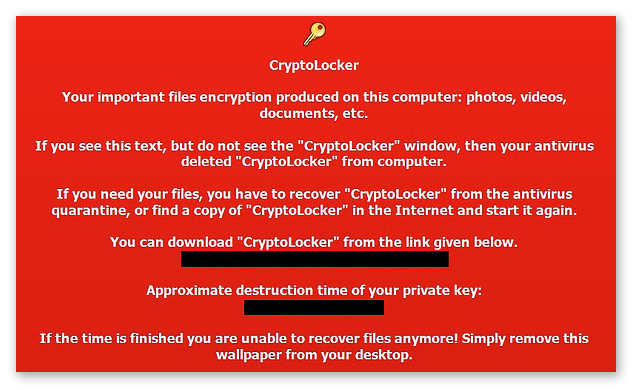
Because CryptoLocker launches any time an infected computer is turned on, it’ll also provide you with a rapidly-declining payment window. Note how the ransom note above actually instructs victims to re-download the malware in the event their own antivirus deleted it.
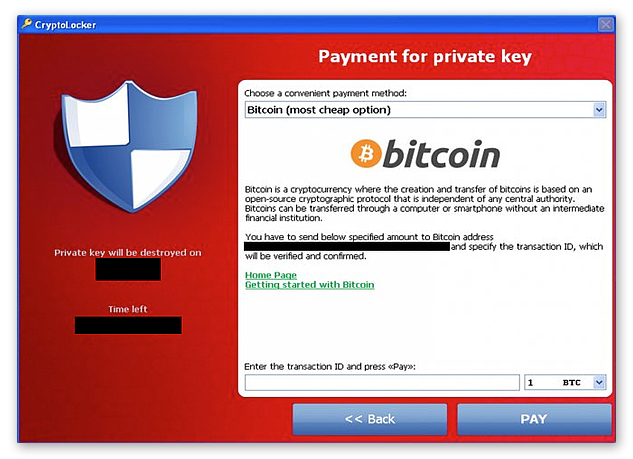
CryptoLocker informs victims that their “private key” — the thing they need to pay for, and which will theoretically decrypt their files — will be destroyed within a certain amount of time if payment is not received. In November 2013, a few months after the attack had commenced, the cybercriminals behind CryptoLocker introduced an online service that promised to unlock victims’ files after their deadlines had passed, but for a significantly higher fee.
How to remove CryptoLocker ransomware?
To remove CryptoLocker from your computer, all you need to do is fire up a trusty antivirus program, such as Avast One. It’ll scan your computer for any hints of malware, including ransomware like CryptoLocker, and expunge it from your machine.
It’s so easy that, as mentioned above, CryptoLocker’s creators anticipated that many people would have antivirus software that already deleted the ransomware.
That CryptoLocker’s potential removal was not a deterrent to its use tells us something: removing the ransomware doesn’t solve the problem. Once CryptoLocker encrypts your files, they’ll stay encrypted until you decrypt them with the correct key. Removing CryptoLocker prevents it from encrypting anything else, but it isn’t going to decrypt your files.
When infected with ransomware, you may be tempted to pony up the ransom in the hopes that the cybercriminals will furnish you with the decryption key you need, but there’s no guarantee that this will happen. They may instead elect to abscond with your money, leaving you both poorer and still without your files. Some types of ransomware encryption can’t even be reversed in this way.
Paying ransoms sends the message that using ransomware to extort people is a viable and profitable pursuit. You can help spare future victims by showing cybercriminals that you won’t cave to ransomware. Never pay a cybercriminal to recover your files.
Instead, the most reliable way to recover your files is by restoring them from a backup. That’s why it’s so important to perform regular backups of all your important data. But first, remove the ransomware from the infected device:
How to decrypt files encrypted by CryptoLocker
When cybersecurity researchers crack a ransomware strain’s encryption methods, they’ll often release a free decryptor online. While a CryptoLocker decryptor tool was released in the wake of Operation Tovar, researchers haven’t yet beaten all of CryptoLocker’s many clones and descendents.
If you’ve been affected by an uncracked strain, you won’t be able to benefit from the decryptor tools. Instead, and as described above, your best bet is to remove the ransomware and restore your files from a backup, if you have one. If not, do not delete your files! Encrypted files can’t be opened, but there’s no harm in waiting for a cure. As research progresses, it’s possible that more CryptoLocker decryptors will come online in the future.
Again, we’ll urge you never to pay a cybercriminal’s ransom. You simply can’t be sure that you’ll get anything in return.
Is CryptoLocker ransomware still a threat?
Since Operation Tovar cracked CryptoLocker’s encryption keys, you’re no longer at risk of infection from the original variant. Due to its resounding success, the CryptoLocker name (and a family of variations on this theme) has been used by several other instances of ransomware.
CryptoWall, first appearing in 2014, infects Windows 10 in addition to older editions. CryptoWall embeds itself in the infected computer’s startup files. It was so successful that in 2015, an FBI agent admitted that in many cases, the agency actually encouraged victims to pay the ransom in order to recover their files — the debateable soundness of this advice notwithstanding.
So while the original CryptoLocker isn’t going to present much of a threat anymore, there’s plenty more ransomware out there just dying to sink its claws into your files.
How to prevent CryptoLocker ransomware?
CryptoLocker can only encrypt the files and folders to which its user account has access. If you’re administering a network, you can help mitigate the potential damage by granting users access only to the resources they are likely to need — a setup known as the least privilege model. Though when it comes to protecting your personal computer, this CryptoLocker prevention strategy is not likely to have any relevance.
Instead, be sure to always follow these anti-ransomware best practices to prevent CryptoLocker and other ransomware from infecting your computer:
-
 Back up your data. This tip comes first because it is the single most effective way to recover your files in the event that you get hit with ransomware. If you use an external drive, disconnect it after the backup is complete and store it in a safe place. If you leave it connected to your computer, the ransomware can encrypt it as well. You can (and should) also back up to cloud services. With a fresh backup at the ready, ransomware won’t mean a thing to you.
Back up your data. This tip comes first because it is the single most effective way to recover your files in the event that you get hit with ransomware. If you use an external drive, disconnect it after the backup is complete and store it in a safe place. If you leave it connected to your computer, the ransomware can encrypt it as well. You can (and should) also back up to cloud services. With a fresh backup at the ready, ransomware won’t mean a thing to you.
-
 Never download attachments from unknown senders. Aside from the Gameover ZeuS botnet, this is how CryptoLocker made its way onto the computers of its victims. No matter what, never download unknown attachments. It’s also good practice to verify any attachments that come from trusted contacts of yours. “Hey, did you mean to send me this?”
Never download attachments from unknown senders. Aside from the Gameover ZeuS botnet, this is how CryptoLocker made its way onto the computers of its victims. No matter what, never download unknown attachments. It’s also good practice to verify any attachments that come from trusted contacts of yours. “Hey, did you mean to send me this?”
-
 Don’t click unknown links. The same advice applies here as to the above tip. If you’re shown a link from an untrusted source, leave it alone. Not only in emails, but on the internet as well, especially in comment sections and forums. The links may lead to malicious websites that automatically download malware, including ransomware, to your computer.
Don’t click unknown links. The same advice applies here as to the above tip. If you’re shown a link from an untrusted source, leave it alone. Not only in emails, but on the internet as well, especially in comment sections and forums. The links may lead to malicious websites that automatically download malware, including ransomware, to your computer.
-
 Download programs, apps, and content from verified sources. When you download from official portals, you’re benefiting from the additional security of a thorough vetting process. P2P file sharing can be a tempting method for obtaining the content you want, but you do so at your own risk.
Download programs, apps, and content from verified sources. When you download from official portals, you’re benefiting from the additional security of a thorough vetting process. P2P file sharing can be a tempting method for obtaining the content you want, but you do so at your own risk.
-
 Always update your software. Install updates and patches as soon as they’re released for your operating system and other software. These often eliminate vulnerabilities that cybercriminals can otherwise exploit to get their malware onto your computer.
Always update your software. Install updates and patches as soon as they’re released for your operating system and other software. These often eliminate vulnerabilities that cybercriminals can otherwise exploit to get their malware onto your computer.
-
 Limit the personal information you give away or put online. The more of your personal info a cybercriminal has, the more accurately they can tailor a phishing attempt to you. Be an active participant in maintaining your online privacy.
Limit the personal information you give away or put online. The more of your personal info a cybercriminal has, the more accurately they can tailor a phishing attempt to you. Be an active participant in maintaining your online privacy.
-
 Use security software. Strong cybersecurity software can do a lot of the prevention for you. Equip your computer with antivirus software to block malware before it has a chance to install itself, and use a VPN to stay protected while on public Wi-Fi.
Use security software. Strong cybersecurity software can do a lot of the prevention for you. Equip your computer with antivirus software to block malware before it has a chance to install itself, and use a VPN to stay protected while on public Wi-Fi.
Defend against CryptoLocker with a dedicated anti-ransomware tool
Upgrade your cybersecurity with Avast One, the world-leading anti-ransomware solution. It’s continually updated to keep you ahead of the latest online threat developments. Our top-rated antivirus and comprehensive security software alerts you to any out-of-date software that might leave your system vulnerable while also detecting and blocking ransomware before it can land on your device.



 The
The 












