Ryuk ransomware continues to be evolved by cybercrime groups, such as WIZARD SPIDER and their offshoot GRIM SPIDER. The emergence of a new variant in January 2021 has seen Ryuk ransomware develop worm-like capabilities, enabling the malware to spread automatically within networks that it enters, like a virus. This allows it to spread itself from system to system within a Windows domain without a human operator. By replicating itself rapidly, it further reduces the time taken to infect networks and devices, posing a danger to businesses.
Why should businesses safeguard against Ryuk ransomware?
Since its inception in 2018, Ryuk ransomware has become one of the most advanced ransomware types. It is highly sophisticated in its delivery, harnessing a wide-reaching knowledge of a target business and its operations. Its victim of choice? Businesses, organizations, hospitals, and institutions that house confidential and sensitive data within outdated operating systems and infrastructure.
Learn more about Ryuk ransomware below and discover how you can protect your business from malware.
What is Ryuk ransomware?
Ransomware is a form of malware that enables attackers to use encryption techniques to infect entire networks (including files and associated devices), making them inaccessible to the target business until a ransom is paid. The ransom is usually demanded in a form of cryptocurrency, such as Bitcoin, and can be thousands, if not millions, of dollars. The average ransom payment reached $12,762 in 2019 and the average cost of incident-related downtime in just one quarter reached $64,645 per company.
Attackers routinely target large organizations or businesses with highly sensitive, critical assets, such as hospitals – a technique named “big game hunting.” Additionally, unlike with other forms of ransomware, cybercriminals using Ryuk malware target specific individuals and manually infiltrate the company’s networks. Using open-source tools available on the network, attackers harvest sensitive data and gain access to as many areas of the business as possible, gaining a detailed knowledge of internal operations.
History
Based on Hermes, an older ransomware, Ryuk ransomware was first identified in 2018 and is widely thought to have been adapted and developed by a cybercriminal organization in Russia. Since 2019, criminal groups have increased the number of attacks, obtaining millions of dollars in ransom payments from financial institutions, hospitals, and even local governments.

How does Ryuk target businesses?
Like most malware, Ryuk ransomware is delivered through several means:
- Sending a spam or phishing email with an infected attachment that, when opened, allows the hacker to obtain remote access to your network
- Sending a spear-phishing email, where the Ryuk attacker targets groups or organizations by impersonating someone within or related to the company. All emails with a Ryuk ransomware attachment can also be sent from a spoofed (forged) email address, allowing attackers to evade detection.
- Through an RDP port, taking advantage of weak security protections and enabling hackers to remotely access your system.
In some Ryuk attacks, the network is first infected with a Trojan (malicious content hidden within seemingly legitimate code) known as Emotet. The Trojan is used as a ‘dropper’ to download Trickbot, another form of malware. This is done to multiple systems, allowing the attacker to monitor multiple targets, and access sensitive information and administrative credentials. The cybercriminal then deploys Ryuk to their chosen target.
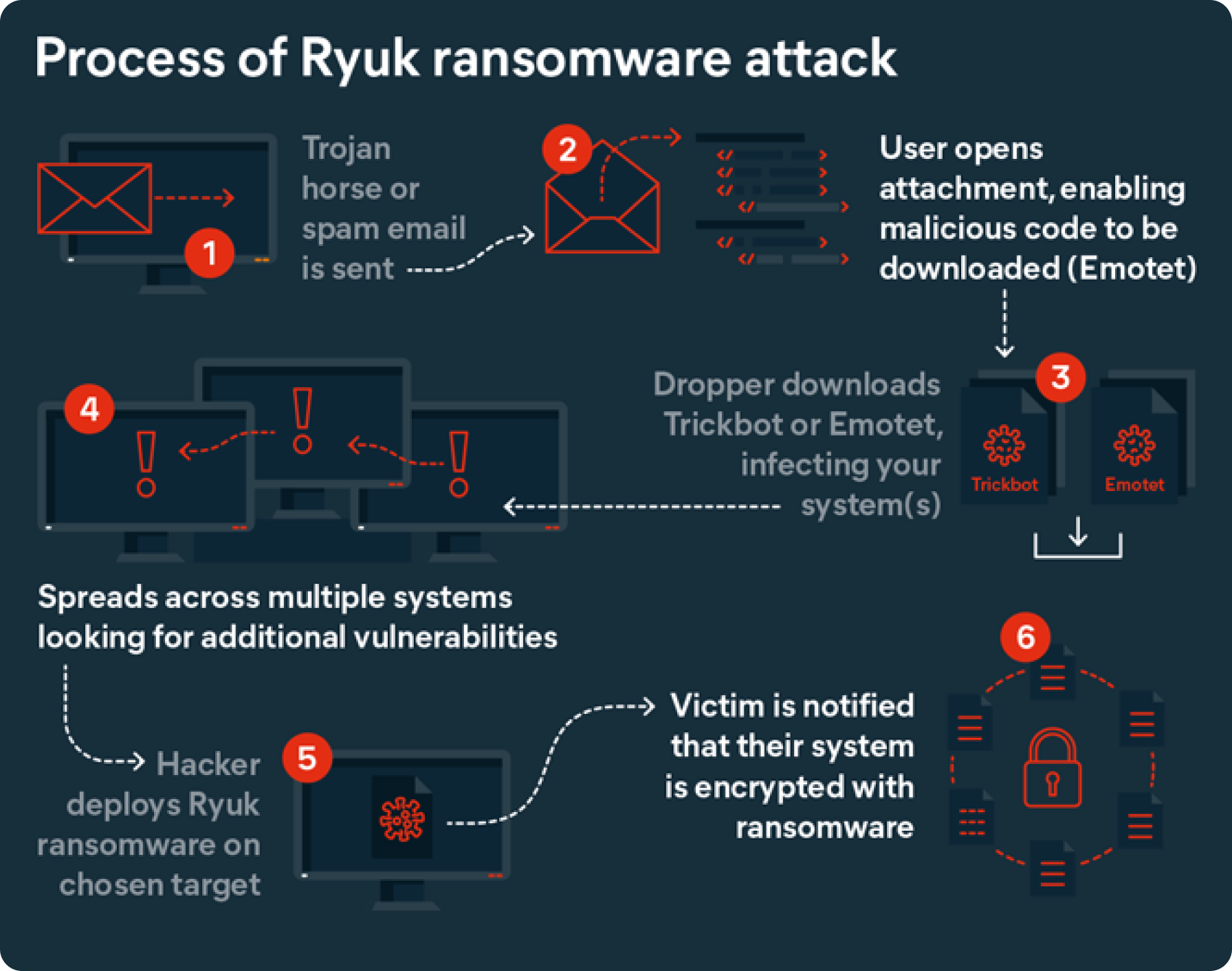
Similar to Locky ransomware, Cerber ransomware, and REvil/Sodinokibi ransomware, once the threat actor has breached your network and server security with Ryuk ransomware, it will shut down up to 180 services and 40 processes that your system needs to operate and will lead to your critical information being encrypted.
Once your files have been encrypted, Ryuk ransomware deletes the original copies and any shadow copies using a .BAT file. This means that all attempts by victims to recover their data will fail.
Ryuk uses both symmetric encryption and asymmetric encryption algorithms to encode files – a similar method to that of Petya and Mischa ransomware, which utilizes several methods to encrypt user data.
Impacting all files and applications across the network, the Ryuk ransomware, once it has fully achieved its goals, will drop into every folder a text file called “RyukReadMe.txt” that puts forth the ransom request details required. If a ransom is paid, as the cyberthieves claim, a copy of the encryption key will enable files to be retrieved.
Examples (famous attacks)
As the number of Ryuk ransomware attacks continues to rise, governments and businesses must remain vigilant. Some of the most high-profile Ryuk attacks since 2018 include:
- Hospitals in the US, Germany, and the UK (2019-2020): Various hospitals in these countries were all victims of repeated Ryuk malware attacks. In September 2020, Universal Health Services (UHS), which operates facilities across the UK and US were hit with Ryuk malware. The incident cost the company $67 million and took a month for all operations to resume. A network of over 400 hospitals in the US and UK were also impacted by Ryuk malware in September 2020, with all 250 facilities in the US affected in one of the largest medical Ryuk attacks to date. Ryuk malware was reportedly responsible for 75% of attacks on the US healthcare sector in October 2020.
- Lake City, Florida (2019): Following an employee’s decision to open an email that housed a form of Ryuk malware, the city’s IT systems were held for a ransom of $460,000. The Mayor of Lake City confirmed that the city authority paid the ransom request to regain access to its operations.
- City of Onkaparinga, South Australia (2019): In December 2019, the IT systems of Onkaparinga Council in Adelaide were infected with Ryuk ransomware, costing a week of lost productivity.
- EMCOR (2020): In February, Fortune 500 company EMCOR confirmed that several of its IT systems were affected by a Ryuk malware attack. The company has not confirmed whether a ransom payment was made.

How to protect your business against Ryuk
It was predicted that ransomware would cost businesses $1.85 million in 2021 and will cost the world $265 billion by 2031. Businesses that understand how to prevent ransomware attacks can significantly reduce their online vulnerability. At present, several factors could increase your risk of being targeted, including outdated software or devices, unpatched browsers and/or operating systems, weak or non-existent backups, or a lack of investment in cybersecurity protection tools.
It is vital to ensure that your systems remain regularly updated from new and upcoming cyberthreats by installing antivirus and anti-malware solutions across your business network. This software should also be supported by other defensive mechanisms, such as:
- The implementation of a Disaster Recovery Plan: This can underpin the processes and protocols across your organization, and define the roles for individuals and contacts that will need to be notified in the event of a cyberattack.
- Role-Based Access Control: Introducing backups and least privilege access should be deployed to minimize the risk of ransomware attacks. Role-Based Access Control (RBAC) can also provide an additional layer of security by limiting employee access to data they do not need for their specific job requirements.
How do I remove Ryuk ransomware from my operations?
While it may be possible to remove Ryuk ransomware from a PC or Mac, it is not guaranteed – the malware continues to evolve and pose new challenges for organizations.
Implementing preventative measures, such as installing anti-malware protection, can protect your business from any cybersecurity threats and incorporate regular updates on software and applications, including patches to fix any vulnerabilities on your network.
Ryuk continues to significantly impact business performance
Ryuk and other types of malware continue to evolve as criminal groups continue to share and adapt dangerous malware, and businesses will need to keep abreast of all threats to business security. Ryuk ransomware has also now been adapted to attack web servers and it harnesses the capabilities of a worm, further impacting operations.
To reduce the risk of malware, robust server security will also be essential, and your chosen cybersecurity solution should look to bolster business performance as well as block, detect, and prevent the risk of attack.
Protect against ransomware with Avast Small Business Cybersecurity Solutions
Keep your business safe from ransomware and the latest cyberattacks with Avast Small Business Cybersecurity Solutions - simple, powerful, and affordable online security for your small business that you can trust to keep you protected. Get peace of mind with this all-in-one solution.
