Current computer viruses, malware, and other threats in 2024
The threat landscape is constantly evolving as cybercriminals find new ways to get modern computer viruses and other malware onto devices and networks. But the one constant is that the malware threat continues to grow and advance.
A conspicuous development in 2023 was in ransomware, which saw the month of March break ransomware attack records with a 62% year-over-year increase. This trend has broadly continued in 2024, with ransomware attacks at an all-time high month-over-month and year-over-year.
But while ransomware may be one of hackers’ favorite ways to profit from cybercrime, other types of malware remain a constant scourge, and increasingly sophisticated attack vectors including trojans and drive-by downloads make malware of all kinds harder to defend against.
Here are the top computer malware threats to beware of in 2024:
-
RaaS
-
LockBit 3.0
-
8Base
-
SocGholish
-
Clop
-
Akira
-
Windows Update Ransomware (Cyborg)
1. RaaS
In the past, ransomware was limited to bad actors with the knowledge and ability to create their own software. That has changed with the rise of Ransomware as a Service (RaaS). Anybody can now pay “professionals” to carry out sophisticated attacks for them.
RaaS is a worrying trend as it makes sophisticated malware tools available to hackers with little or no experience, helping to make ransomware attacks more widespread and unpredictable. As this new level of access to malware develops, the number of unexpected and erratic attacks enabled by RaaS groups looks set to increase in the coming years.
LockBit remained the most established and widespread RaaS in the first quarter of 2024, with 217 declared successful attacks accounting for more RaaS extortion attacks than those performed by 8Base and BlackBasta — the next two largest ransomware groups — put together.

2. LockBit 3.0
The LockBit ransomware group has been active since 2020. What makes LockBit 3.0 different from previous versions of the group’s malicious software is it has become modular, meaning that the malware infects a system in stages, making it much harder to detect and prevent than older, less stealthy iterations.
Here’s a closer look at recent LockBit incidents:
-
LockBit was used to steal 3,000 blueprints and schematics from Space X parts manufacturer Maximum Industries.
-
A claim by the LockBit group that they’d taken data from TSMC, a semiconductor manufacturer, and demanded a ransom of $70 million.
-
The discovery of a new sub-variant of LockBit 3.0 with self-spreading features that mimic traditional computer virus promulgation.
-
After the UK’s National Crime Agency (NCA), the FBI, and Europol organized a joint disruption against the LockBit operation, including taking over websites used by the ransomware group, LockBit launched attacks from new servers using updated encryptors.
 The message showing on LockBit sites seized by law enforcement agencies. Source: Avast 2024 Threat Report and the BBC.
The message showing on LockBit sites seized by law enforcement agencies. Source: Avast 2024 Threat Report and the BBC.
3. 8Base
The 8Base ransomware group has been active since March 2022, with more than 356 victims having fallen prey by May 2024. The group gained significant attention in June 2023 after a dramatic increase in activity.
8Base tends to target businesses with a double extortion approach — stealing and encrypting the data before using name-and-shame tactics to secure ransom payments. They share similarities with another group, RansomHouse, which has spawned rumors that 8Base is an offshoot. And there’s still uncertainty about the intentions and approach behind 8Base.
4. SocGholish
SocGholish accounted for 60% of the top ten malware strains impacting Windows users in early 2024, making it one of the year’s biggest threats. Also known as FakeUpdates, SocGholish has been around since at least 2017.
It’s a downloader that is delivered by a drive-by-download, where the user unwittingly downloads malware from a compromised or malicious website, having been tricked into clicking fake software or browser-update links.
Here’s how SocGhollish malware attacks usually unfold:
-
Fake browser updates: Hackers create malicious websites or compromise legitimate ones to show fake software update alerts that closely imitate real update notifications from popular browsers.
-
Malicious downloads: If a user falls for the fake update, they are then redirected to a download page, and the apparently harmless file is downloaded and executed without any further interaction.
-
Secondary malware: Secondary malware like remote access trojans (RATs) may then be deployed to control the system or steal sensitive data.
5. Clop
Clop ransomware (also known as CLOP, Cl0p, and TA505) is considered one of the most dangerous threats to data security today. It’s a modernized version of CryptoMix, first identified in 2016, that targets Windows PCs. The Russian gang responsible for the ransomware has claimed ownership over many major data breaches, including attacks on the BBC and British Airways.
The danger posed by Clop ransomware made headlines throughout 2023, as the malicious code targeted multiple businesses, US federal government agencies, and state governments in Minnesota and Illinois. Johns Hopkins University in Baltimore and Georgia’s state-wide university system were victims of Clop attacks during the same period.
"The Russian gang responsible (for Clop) has claimed ownership over many major data breaches, including attacks on the BBC and British Airways."
In response, CISA and the FBI published a warning about the Clop ransomware gang, revealing that the cybercriminals had used SQL injection to exploit a vulnerability in the MOVEit data transfer software. The vulnerability allowed them to access data hosted by the service, including sensitive information on government agencies and individual users.
6. Akira
Akira is one of the latest ransomware threats to gain mass attention thanks to a reputation for demanding hundreds of millions in ransom payments. Because of these enormous fees, it’s unlikely that corporate victims will see their stolen data again — unless it’s made public on the group’s site on the dark web.
Akira is a deeply concerning emerging cyberthreat and has been linked to several high-profile attacks, including:
7. Windows Update Ransomware (Cyborg)
One of the basic principles of cybersecurity is to ensure that devices are running the latest operating systems and software. But some hackers take advantage of this to prey upon their victims with bogus updates containing malware.
Although Windows update ransomware is not a new attack vector, innovative ransomware continues to be developed to exploit fake installation update emails claiming to be from reputable software companies like Microsoft.
One of the most common types of malware used in these attacks is known as Cyborg ransomware, a fairly typical form of ransomware that first emerged in 2019. Once active, Cyborg sweeps through the target PC, encrypting every file it can find.
Global threat activity
The sheer scale of the threat posed by malware is a serious concern for both individuals and organizations around the world. According to Gen’s Threat Report from the second quarter of 2024, there was a 46% year-over-year increase in observed cyberattacks in the April-to-June period, with scams as the dominant threat and browsers and the web making up the primary attack surface.
Widespread cyberattack activity is reflected in SoSafe’s Human Risk Review of 2024, which found that half of the organizations surveyed had suffered a successful attack at some point during the previous three years. The potential for devastating, system-level attacks is underscored by a 2023 study that found that 43% of all ransomware attacks accessed PowerShell, while an astonishing 91% of all attacks exfiltrate data.
The threat isn’t limited to private companies and organizations. The US military has been actively searching its systems for malware believed to have been planted by Chinese actors. If left unchecked, US administration officials fear malicious code could disrupt power grids, communication systems, water supplies, and other critical military and civilian infrastructure.
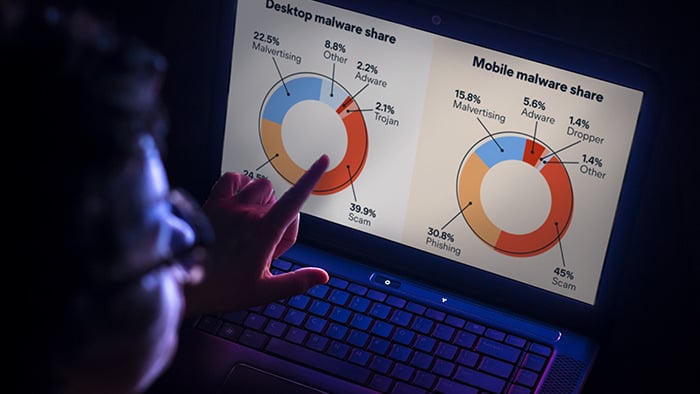
In addition, social engineering techniques are now the primary attack vector for mobile and desktop malware, meaning that scams and phishing communications eclipse the danger posed by more traditional malware such as trojans or adware. In other words, rather than software vulnerabilities, humans are now the most exploited gateway for viruses and other malware.

For more, check out the Center for Strategic and International Studies’ timeline of significant cyberattacks impacting government agencies and other high-value targets around the world.
Thankfully, the latest cybersecurity tools are able to help prevent attacks from new and emerging threats. Avast’s Threat Report from the first quarter of 2024 showed that Avast blocked more than 3 billion attacks and more than 500 million dangerous URLs over the three-month period.
The future of AI viruses and malware
One of the greatest challenges in the field of cybersecurity today is the rise of AI-powered viruses and other malware created with the help of custom AI hacking tools like Worm GPT.
BlackMamba
Researchers developed sophisticated proof-of-concept malware called BlackMamba that can leverage artificial intelligence to dynamically generate malicious payloads. This unique approach makes detection difficult, as the malware can change its signature to evade traditional defenses.
BlackMamba is capable of keylogging, stealing sensitive information, and establishing remote access to compromised systems. Its advanced obfuscation techniques and adaptive nature represent a significant challenge for security professionals to keep up with evolving threats.
Phishing scripts
Generative AI will also help hackers create in high volume more sophisticated and convincing phishing scripts. And it will be very difficult for security professionals to identify and protect against such highly personalized phishing emails that use deepfake audio and video to mimic legitimate communications.
 AI-powered phishing attacks are becoming more sophisticated and harder to detect.
AI-powered phishing attacks are becoming more sophisticated and harder to detect.
Even now, alarming findings from SoSafe show that a third of users click harmful content in phishing emails — and half of them go on to enter sensitive information. What that means for the future of cybersecurity is still unknown.
As real-life BlackMambas are released into our digital world, and phishing messages become harder to spot, having cutting-edge security software to keep bad actors in check is a must. But a holistic approach is needed, and that means implementing a range of safety measures.
How to protect against the latest viruses and threats
With the complexity of cyberattacks growing, deploying the full spectrum of online security tools and practices is more essential than ever. You can minimize the risk of falling victim to an attack by following the best internet safety tips.
Online safety tips
Multi-factor authentication: Activate two-factor authentication (2FA) or multi-factor authentication (MFA) for your accounts and devices wherever possible.
Password manager: Create strong, unique passwords and use a password manager to keep track of them all.
Install updates: Keep your apps and software updated to benefit from the latest security patches.
Cybersecurity software: Install and use reliable cybersecurity tools such as anti-malware software, firewalls, and VPNs.
Get comprehensive security and privacy protection with Avast
Want to improve your online security and protect your devices from the latest computer viruses? Download Avast One, an all-in-one security solution with real-time malware detection and removal powered by an award-winning threat-detection engine that helps counter new and emerging viruses and other online threats. Get ironclad security today — completely free.


 The message showing on LockBit sites seized by law enforcement agencies. Source:
The message showing on LockBit sites seized by law enforcement agencies. Source: 








/What-is-a-macro-virus-Thumb.jpg)


