- Security
- Privacy
- Performance
The Top Password-Cracking Techniques Hackers Use
Written by
|
Updated on June 28, 2024
Domenic Molinaro
Updated on June 28, 2024
Anyone can become an effective password guesser with freely available password-hacking tools. A password hacker can use an automated password finder to identify their target, and then deploy a powerful password cracker to finish the job. Learn all about password-cracking methods, and how to set up your own personal digital data watchdog with Avast BreachGuard.
Get Avast Breachguard
Get it for Mac
Get Avast Breachguard
Get it for PC
Get Avast Breachguard
Get it for PC
Get Avast Breachguard
Get it for Mac

This Article Contains
This Article Contains
What is password cracking?
Password cracking is when a hacker uncovers plaintext passwords or unscrambles hashed passwords stored in a computer system. Password cracking tools leverage computing power to help a hacker discover passwords through trial and error and specific password-cracking algorithms.
If a hacker discovers your password, they may be able to steal your identity, steal your other passwords, and lock you out of your accounts. They can also set up phishing attacks to trick you into giving up more sensitive data, install spyware on your devices, or sell your data to data brokers.
The best way to protect yourself against cybercriminals and cybercrimes like password theft is with a healthy mixture of common sense and modern security solutions.
How can I prevent my password from being hacked?
You need to understand how to create the most secure passwords, how to keep them safe, and use the right technology to protect against password crackers.
To help prevent your passwords from being hacked, create long and unique passwords for all your accounts. We know it’s super convenient to use your dog’s birthday for all your passwords, but this just makes it more convenient for password hackers. Make sure your passwords are at least 15 characters long and combine a mix of uppercase and lowercase letters, numbers, and symbols.
Bolster your account security by enabling two-factor authentication (2FA) or multi-factor authentication (MFA) whenever possible. This means that if a hacker discovers your password they would still need your other authentication method/s to log in. Given that other verification methods are usually biometrics, a one-time PIN code, or a physical device, this proves challenging for even the best hackers.
Two-factor authentication requires two verification methods to log in to an account.
It’s easy to let your browser save all your passwords for you. But if someone takes control of your computer, either remotely or in person, they can take control of your passwords too. That’s why you shouldn’t save passwords in your browser — and why a password manager is generally the safer way to go. Make sure you choose from one of the best password managers to keep your accounts safer.
You should also use Avast BreachGuard to monitor your password security and get alerts if breaches are detected to help you change your compromised passwords faster and minimize the damage. Download Avast BreachGuard today to strengthen your password security and get expert support when you need it most.
What is a hashing algorithm?
A hashing algorithm is a cryptographic function that turns a plaintext password into a string of letters, numbers, and special characters. It’s practically impossible to reverse a hashing algorithm, but hackers can find the original password with the help of password-cracking software.

Hackers use password-cracking software to find a plaintext password.
As hackers learn to crack hashing algorithms, newer and stronger hashes are developed. Some popular — though now obsolete — password hashing algorithms include MD5 (Message Digest Algorithm 5) and SHA-1 (Secure Hashing Algorithm 1). Today, one of the strongest password hashing algorithms is bcrypt.
Common password hacking techniques
The first step to cracking passwords is stealing the hashed versions, often by cracking a system or network that holds the passwords. Hackers can target a company’s software vulnerabilities through exploits and other hacking methods to get at the passwords inside.
From there, it’s just a matter of choosing the right password-cracking techniques and tools. Individuals typically aren’t hacking targets — the aim is to cast a wide net and catch as many passwords as possible.
New password attack methods are developed every day. Luckily for hackers, human password habits haven't developed alongside. Many classic rule-based programs and algorithms are still effective in predicting people’s password choices.
Sometimes all a hacker has to do is wait for a data breach to leak millions of passwords and private details. Hackers often share and trade sensitive data they find, so it pays to have privacy software like Avast BreachGuard that monitors the web for your sensitive details to help prevent companies from selling your personal info and protect you from snoops and fraud.
Brute force attack
A brute force attack is when hackers use computer programs to crack a password through countless cycles of trial and error. A reverse brute force attack attempts to crack a username through the same method.
Modern computers can crack an eight-character alphanumeric password or ID in just a few hours. Many freely available online brute force tools allow nearly infinite guesses of a target’s login credentials, such as the popular and notorious Brutus password cracker.
The worst passwords are sequential letters and numbers, common words and phrases, and publicly available or easily guessable information about you. These simple passwords are incredibly easy to crack via brute force, and they could end up in a data breach sooner or later.

Brute force attacks are especially effective against easy-to-guess passwords without symbols.
Hackers compile cracked usernames and passwords into a hitlist for attacks on other networks and systems in a technique called credential recycling. The cycle of hacker violence goes round and round — and your private data is at the center.
Dictionary attack
A dictionary attack is a type of brute force attack that narrows the attack scope with the help of an electronic dictionary or word list. Dictionary attacks target passwords that use word combinations, variations on spellings, words in other languages, or obscure words that are too slippery for a regular brute-force attack.
Because a dictionary attack uses a set list of actual words, passwords that have random special characters are a lot more unpredictable and thus safer against these attacks. Despite this, many people use a regular word as their password because it’s easier to remember.
But using just one obscure word won’t help — a hacker can scour all the dictionaries in the known universe in a matter of moments with an online password cracker.
Mask attack
A mask attack reduces the workload of a brute force attack by including part of the password a hacker already knows in the attack. If a hacker knows your password has 10 characters, for example, they can filter the attack for passwords of only that length.
Mask attacks can filter by specific words, numbers within a certain range, special characters the user prefers, or any other password characteristics the hacker is confident about. If any of your data is leaked, it makes you more vulnerable to a full-on breach.
If your credentials are leaked in a data breach, they may end up on the dark web.
Social engineering
Social engineering is a technique where criminals manipulate people into giving up compromising information. In the context of hacking, social engineering a password is when hackers trick someone into divulging their password details, such as by pretending to be tech support.
It’s often easier to gain someone’s trust than it is to gain access to their computer, especially if the scammer isn’t tech-savvy.
Cybercriminals can get your passwords through tech support scams or other schemes.
Social engineering takes many forms, especially in the age of social media. Ever come across a quirky social media quiz asking you to enter your first pet and street to create a superhero name? A hacker may be trying to social engineer the answers to your password security questions.
Spidering
Spidering is when hackers crawl a company's social media accounts, marketing campaigns, or other corporate material to gather a word list for a brute force or dictionary attack. Spidering can become social engineering when hackers infiltrate businesses for physical handbooks and training manuals full of keywords.
By studying a business’s product, a hacker can glean corporate lingo to compile into a word list for cracking. Default company passwords commonly relate to a brand’s identity, and often remain unchanged. Employees may choose passwords relating to their job since it's easier to remember. With larger companies, spidering is especially effective since there is so much material to sift through.
Shoulder surfing
Shoulder surfing is a social engineering technique of spying over someone's shoulder as they enter login details. Shoulder surfing is a common way to discover ATM PINs, which is why most people are wary of their surroundings while taking out money.
But hackers can also shoulder surf your email for password-cracking intel, or watch your keystrokes as you tap away at an internet cafe.

A password hacker can learn a password simply by peering over your shoulder as you type it.
Offline cracking
Offline cracking is when hackers transfer hashed passwords offline to crack them more safely and efficiently. Online attacks are vulnerable to discovery, can trigger a lockout after too many attempts, and are hampered by a network's speed. With offline cracking, a hacker is invisible, can attempt infinite logins, and is limited only by their own computer power.
Hashed passwords can be taken directly from a database by tried-and-true hacker techniques such as SQL injection. If a hacker gains administrator privileges, it's game over for all the passwords on the admin's system. Learning how to password-protect files and folders can save admins from a disastrous password breach.
But forward-thinking and acting alone can’t protect you from data breaches. Our data is floating all around the web and some of it we share ourselves, other data might be hacked and sold illegally, and data brokers make it even easier for other third parties to view our data neatly in one place. Use Avast BreachGuard to help stop companies from selling your data and keep your data safer.
Password guessing
When all else fails, cybercriminals can collaborate as an effective password-guessing collective. A hacker hivemind is far superior to a single human’s powers of memory.
In today’s global network, it takes only a few clicks and a little know-how to get details on any internet user. And with modern password-cracking tools and tech at their fingertips, it’s only a matter of time before a patient password guesser cracks a weak password.
Password guessers can use personal details found online to crack simple passwords.
Rainbow table attacks
Passwords aren’t stored as plaintext in computer systems but are hashed using a cryptographic function. As this is a one-way function, they can’t be decrypted. Rainbow table attacks use a precomputed rainbow hash table to crack passwords stored in a system by reversing the process and finding a matching hash value for a corresponding password.
The worst passwords are the easiest for these hackers to crack. Common words and patterns like “password” and “12345” will likely be on the table, whereas a completely unique password won’t be and will remain safer.
Phishing for passwords
Phishing is a form of social engineering where the attacker aims to trick the target into divulging their password. They usually do this by pretending to be from a trusted organization like a bank. The scammer invents a reason why they need the password — for example, to secure a hacked account immediately.
Phishing attacks can take the form of vishing (over phone calls or voice messages), smishing (fake text messages), or emails. Attacks launched over texts or emails can include a link to a fake website that’s been spoofed, convincing the victim they’re logging in to a platform they trust.
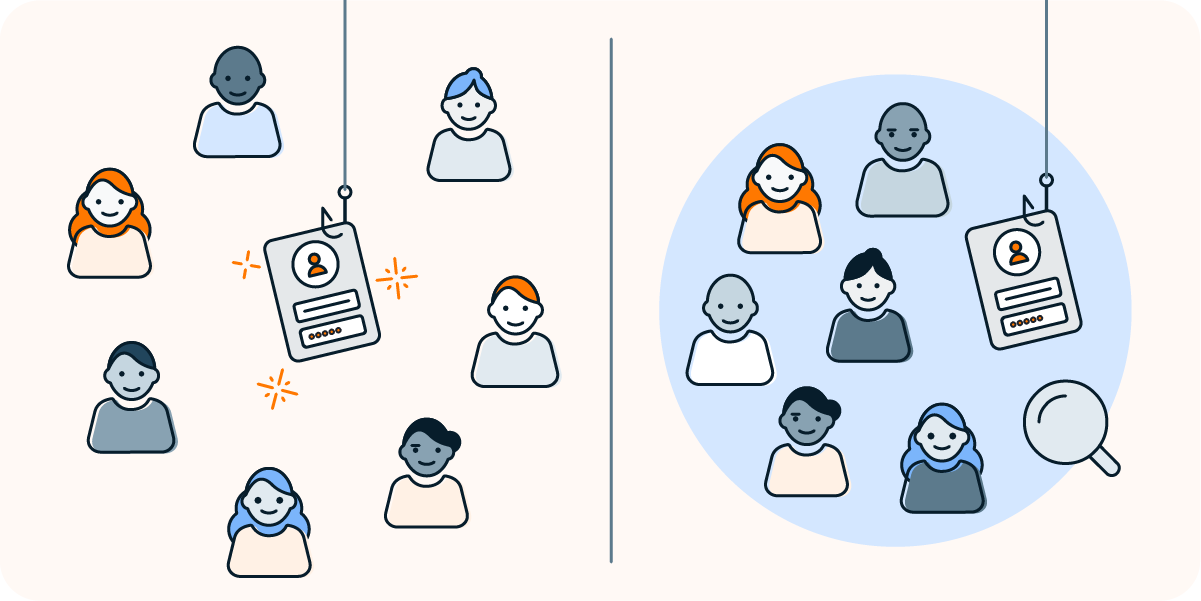
Real passwords are often the goal of phishing attacks.
Keylogging malware
If a cybercriminal manages to infect a victim’s device with a keylogger, it can capture all of their keystrokes, including all the passwords they enter. Keylogging malware is a form of spyware and often runs silently in the background.
Keyloggers can infiltrate a device through malicious links or attachments, often through smishing, phishing emails, or pharming websites. The malware could also be a Trojan — a file, program, or code that’s packaged and delivered inside legitimate software that downloads when the file is opened.
As you can see, there are plenty of ways for cybercriminals to get their hands on your passwords. Use Avast BreachGuard to make your passwords stronger and to unveil potential data leaks so you can act faster and help secure breached accounts. We’ll also share online account security tips to help you keep your accounts safer — with all the password-cracking tools available, you can never be too safe.
Password cracking tools
Along with a slew of techniques and computer programs, hackers can use powerful password tools to seize raw user data for cracking purposes. Any identifying information is valuable to a hacker.
A wily cybercriminal can put the pieces together like a jigsaw puzzle and then get cracking. Hacker communities share hashed passwords, user profiles, credit card numbers, and other lucrative material on the dark web. A dark web scan can show you if your information is up for grabs.
Network analyzers
A network analyzer can inspect a network’s traffic, including network packets with valuable user data inside like passwords. Malware can install an analyzer to spy on data, or someone with physical access to a network switch can plug a network analyzer into it. They are a dangerous modern password hacking tool since they don't rely on exploits or security flaws in a network.
Packet capturing
A packet-capturing tool can act as a sniffer and intercept data packets moving across a network. Hackers use the data to profile potential victims — over time, amassing a trove of password-cracking data. With so much of our data online, password crackers can pluck your private details out of the air. To help keep your data away from hackers, use a secure browser with anti-tracking tech.
How do Instagram passwords get cracked?
Instagram and other social media passwords are extremely difficult to crack — at least in theory. That’s because the platforms use hashing algorithms to convert their users’ passwords into a unique series of randomized characters. But while hash-format passwords are tough to crack, the plain-text passwords remain a weak point.
If your Instagram account has been hacked, it’s extremely unlikely that the hashing algorithm was reverse-engineered. Instead, your plaintext password may have been cracked via a brute-force or dictionary attack, or it may have been compromised in a data breach of a different website. That’s why it’s so important not to reuse identical or similar passwords across multiple platforms — and use a data breach monitoring tool so you can take action quickly if a password is compromised.
Protect your most sensitive data with Avast BreachGuard
If a website you frequent is hacked, it may not matter how careful you’ve been with your passwords and other private details. Data brokers and other third parties collect your personal info, while hackers wait around, looking for any chance to strike.
Avast BreachGuard can help reduce the amount of personal info companies have on you, monitor your passwords to keep them strong, and alert you in the event of a breach. Keep your data safer — get Avast BreachGuard today and put your personal info behind a private security shield.
Get it for Mac
Get it for PC
Get it for PC
Get it for Mac
You Might Also Like...

Is Poshmark Legit?

What to do if you lose your wallet

What Is Riskware and How to Avoid It

Block Mobile Scams Instantly with AI-Powered Scam Guardian Pro

How to Find Hidden Apps on Android

What Is Firmware?
Facebook Session Expired: Causes, Solutions, and Prevention

What is fileless malware, and how can you help prevent it?
Enjoy powerful password protection and peace of mind with Avast BreachGuard
Enjoy powerful password protection and peace of mind with Avast BreachGuard
Browse privately and keep your personal data safer with Avast Secure Browser
Avast
Secure Browser
Browse privately and keep your personal data safer with Avast Secure Browser
Avast
Secure Browser
Enjoy powerful password protection and peace of mind with Avast BreachGuard
Get it nowEnjoy powerful password protection and peace of mind with Avast BreachGuard
Get it nowBrowse privately and keep your personal data safer with Avast Secure Browser
Free installBrowse privately and keep your personal data safer with Avast Secure Browser
Free install