While older forms of ransomware remain, such as Phobos ransomware, new forms of ransomware are constantly being created, and the number of attacks nearly doubled in the first half of 2021. According to Cognyte, 1,097 organizations were hit by ransomware attacks in the first half of 2021 compared to 1,112 in 2020 for the entire year. The US is the most targeted country, accounting for 54.9% of the total victims.
Several factors could increase the risk of your business being targeted, including:
- Having outdated software or devices
- Unpatched browsers and/or operating systems
- Weak or non-existent backup plans to recover your data (leading to increased risk of data loss and reputational damage)
- Lack of investment in cybersecurity solutions.
Preventing ransomware from accessing your systems and defending your business at the initial stages of an attack can save your business thousands, if not millions in recovery costs. A poignant example is the CryptoLocker ransomware attack, which took more than six months to resolve.
Occurring from September 2013 to May 2014, cybercriminals developed a new botnet, named Gameover ZeuS, which formed a network of targets infected with the malware. A script was then sent to the victims via email attachment, which activated the malware once opened. The ransomware was also able to identify other connected devices on the victim’s network, fully encrypting all data or locking operating systems, and halting business operations.
The malware successfully encrypted files and informed victims that their operations were held hostage until payment of a ransom. Attackers obtained millions of dollars throughout their operations.
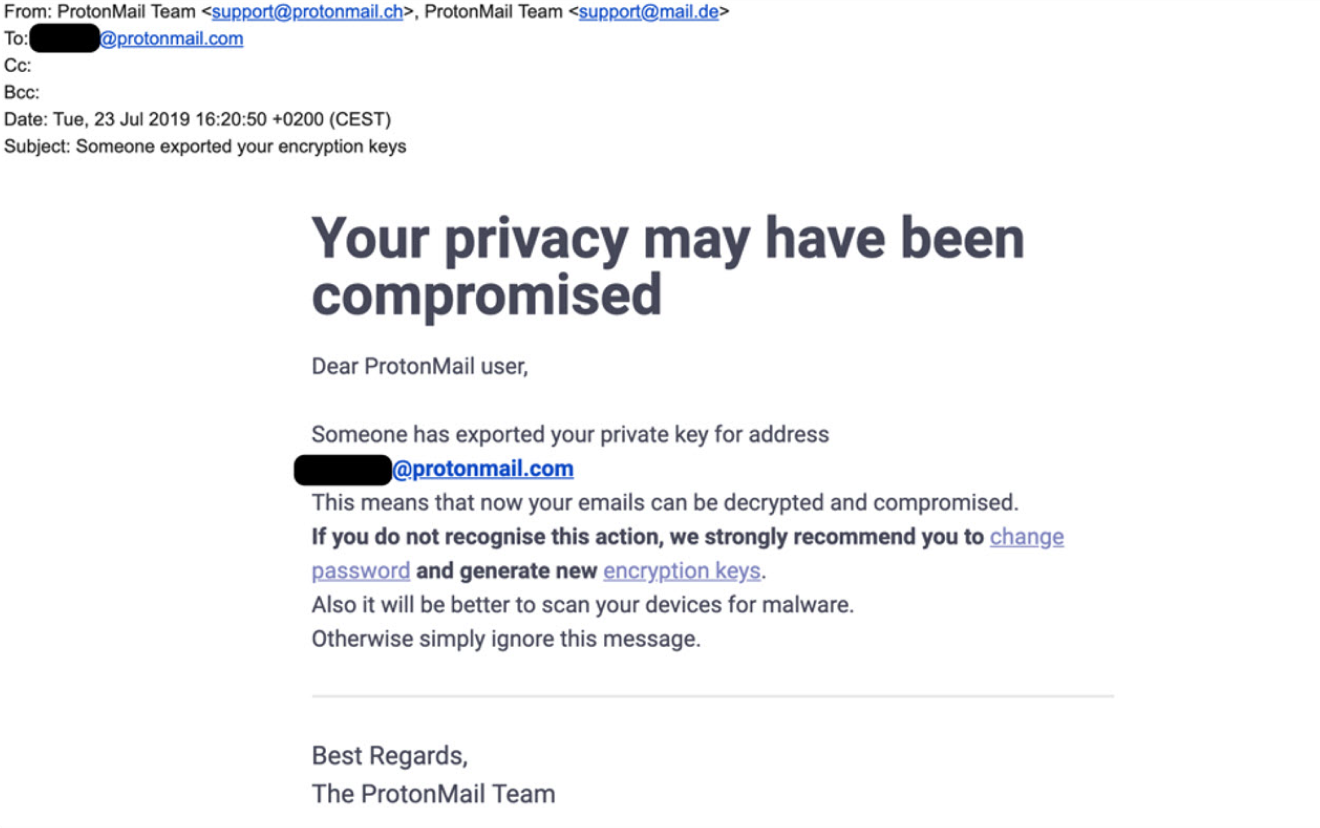
In the CryptoLocker attack, an asymmetric encryption tactic was also utilized. This means that the bad actor could encrypt a file with a public key, while the recipient could only decrypt the system with a private key. Without a private key, recovering the encrypted files was almost impossible.