Protect your Android phone against botnets and other threats with Avast One
- Security
- Privacy
- Performance
A botnet is a network of infected computers that can be controlled remotely and forced to send spam, spread malware, or stage DDoS attacks — without the consent of the device owners. Learn how botnets work and how to protect your computer against them and the malware they often carry with a reliable and free botnet protection tool.
A botnet is a group of computers linked together with malware and controlled by the botnet creator, known as a bot herder. Bot herders infect computers to form botnets, which they control as a group to initiate wide-scale cyberattacks, send spam, and conduct phishing campaigns.

This Article Contains:
The meaning of botnet is “robot network,” and the computers in a botnet are known as bots or zombie computers. Some botnets include hundreds or even thousands of computers, making them one of the biggest online threats today.
Every device in a botnet is linked through the internet to the bot herder, who controls all the computers and uses them to commit a wide range of cybercrimes. Almost any internet-connected device can form part of a botnet, from computers and routers to smart IoT (Internet of Things) devices like TVs and thermostats — the 2016 Mirai botnet predominantly affected IoT devices.
To create and use a botnet, a hacker needs to complete a three-stage attack: infecting victims’ devices, growing the botnet, and finally, activating the botnet.
Infect victims: The bot herder must get their botnet malware onto the computers of their victims. The botnet download and installation is often accomplished via malware or with social engineering tricks.
The hacker may infect victims via Trojan malware (which disguises itself as something harmless), by infecting websites with malvertising ads that can attack visitors, by exploiting security vulnerabilities, or with phishing attacks that trick victims into installing the malware.
Grow the botnet: Zombie computers in the botnet can be used by the bot herder to infect additional devices. Some botnet malware can automatically spread itself by scanning networks for vulnerable devices and infecting them when found.
This technique is especially powerful when the bot herder uses a zero-day vulnerability that can’t yet be countered.
Activate the botnet: When the new botnet has reached a sufficient size, the bot herder can use the combined power of all the infected devices for anything from devastating DDoS attacks to cryptomining.

The three stages of botnet creation and use: infection, expansion, attack.
After infecting a computer or other device, a hacker obtains admin-level access to its operating system (OS) and files. They can use this access to pilfer data from the computer, monitor it while in use, or control its actions.
Here’s what a bot herder in control of a botnet can do with a zombie computer:
Read/write system data: A hacker can not only read the system-level data on a zombie computer, but alter it and write new data as well.
Collect personal data: The bot herder can sift through the files on the zombie computer and harvest sensitive personal data, including passwords and financial information.
Spy on victims: With system-level access, the bot herder can see what anyone using the zombie computer is doing.
Send data: Many botnets are used in mass-email campaigns, such as spam botnets that blast out spam emails. A bot herder can cause zombie computers to send emails, files, messages, and other types of data.
Install apps: Botnets can be the first stage of a larger malware attack. With access to so many computers, bot herders can easily infect all the computers in their network with ransomware, spyware, adware, and other types of malware.
Infect other devices: Zombie computers can scan the networks they’re on for potential victims to infect. This technique is especially potent when the botnet malware spreads through cybersecurity vulnerabilities.
That’s why cybersecurity tools are such a great defense against botnets. Avast One monitors your device 24/7 for any signs of malware, preventing attacks before they happen.
Most botnets take one of two forms: a centralized botnet with direct communication from the bot herder to each zombie computer, and a decentralized system with multiple links between all infected devices.
Centralized: the client-server model
Centralized botnets use the client-server structure of traditional network architecture to communicate with devices in the botnet from a command and control (C&C) server. It’s an efficient system with one glaring weakness — the C&C servers are easy to find and deactivate.
Once the C&C server is taken down, the bot herder can no longer communicate with their botnet.
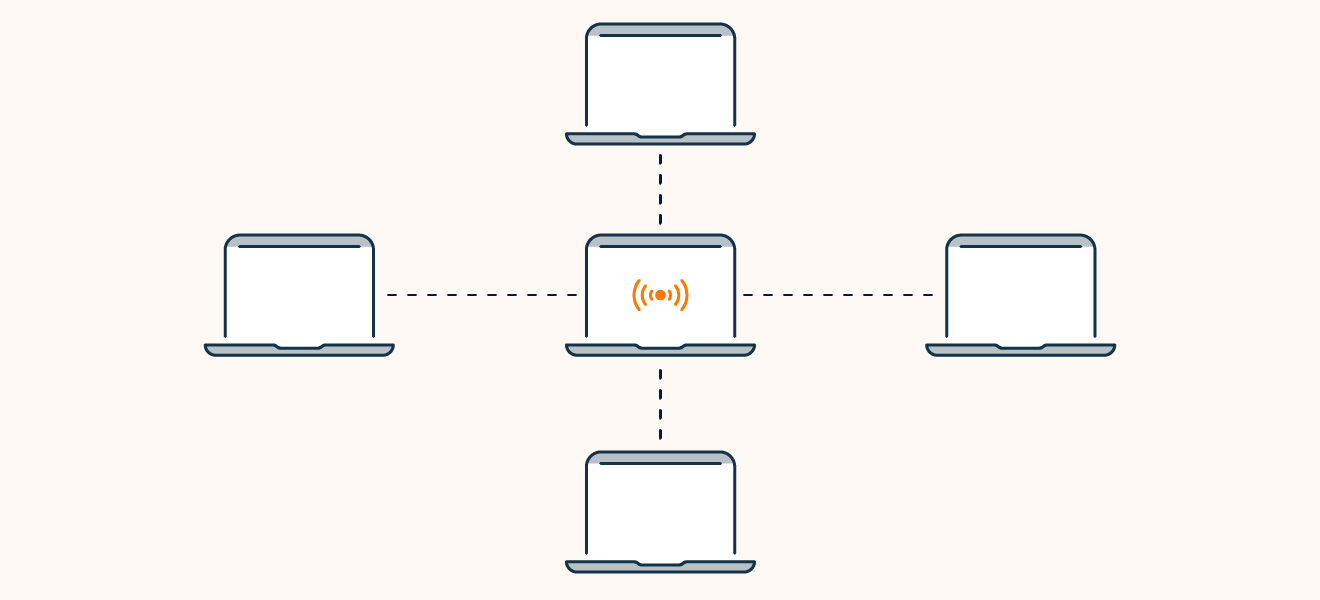 The centralized client-server botnet model.
The centralized client-server botnet model.
Decentralized: the peer-to-peer model
Peer-to-peer botnet models are more advanced, having abandoned the client-server model in favor of a peer-to-peer (P2P) structure with communication spread out across the entire network. Each infected device can communicate with the others, eliminating the need for a single (and vulnerable) C&C server.
Compared to client-server botnets, P2P botnets are much harder to disrupt.
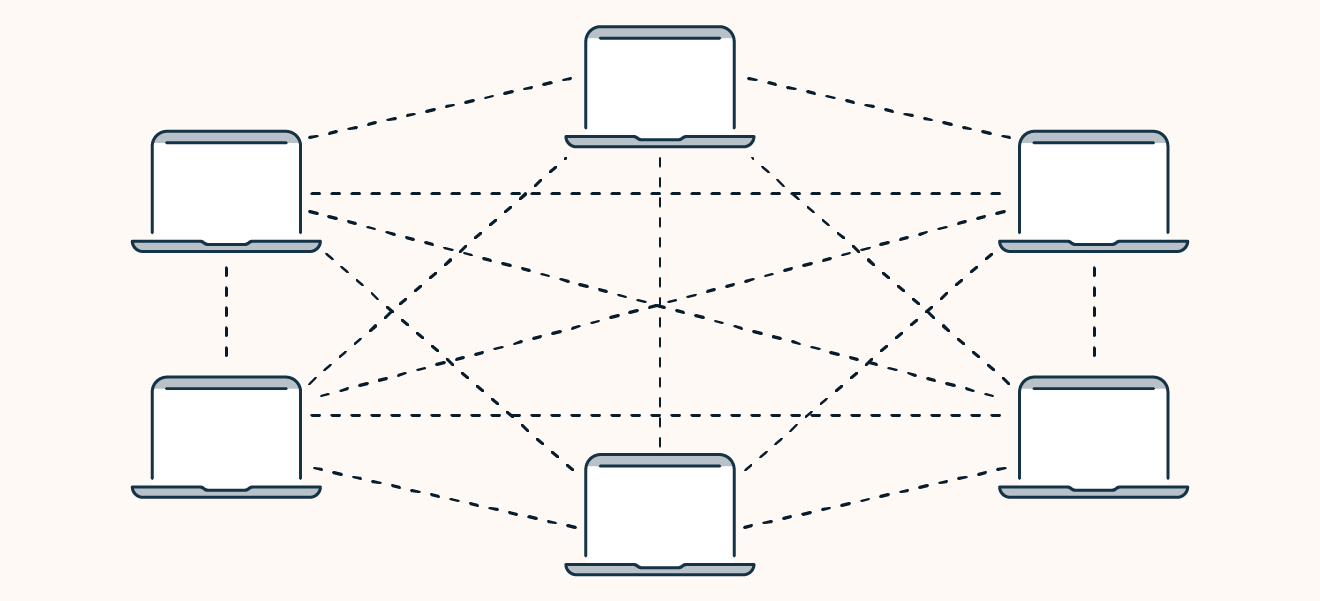 The decentralized peer-to-peer (P2P) botnet model.
The decentralized peer-to-peer (P2P) botnet model.
Launch DDoS attacks: In a distributed denial of service (DDoS) attack, the bot herder causes all the computers in the botnet to overwhelm a server with simultaneous and sustained traffic. This can quickly shut down websites and even entire businesses. A 2019 DDoS attack caused Wikipedia to go offline in several countries around the world.
Conduct spam and phishing campaigns: Botnets are often used in mass-mailing campaigns, since they can send countless emails at once. Spam botnets will send massive amounts of spam, but others may be phishing attacks and other scams.
Mine cryptocurrency: As cryptocurrencies become more mainstream, bot herders are increasingly using their botnets as mining tools. It’s cryptojacking on a massive scale, and all the proceeds go straight back to the bot herder.
Monitor victims and steal personal info: Not all botnets are mobilized in attacks against others. Some bot herders leave their botnets dormant and use them to monitor victims and steal sensitive personal data — including login credentials and financial information.
Infect victims with more malware: A botnet is a readymade target pool for more harmful malware attacks, such as ransomware. With a botnet in place, the bot herder can easily deploy ransomware on the infected computers.
Generate fraudulent ad revenue: In a common scam, bot herders can rent ad space on a website, then coordinate their botnet to “click” the ad en masse. Each click translates into a payment for the bot herder.
Any internet-connected device can potentially be included in a botnet, so long as the bot herder can infect it with botnet malware. Computers, laptops, smartphones, gaming consoles, and even smart appliances can all be included in a botnet.
Smart devices are attractive targets for a bot herder, because weak security is one of the chief risks in the Internet of Things. Many manufacturers don’t protect their smart devices with the same strong cybersecurity measures found in smartphones and computers. And many smart device owners never change their passwords from the factory defaults.
Hackers can exploit these security weaknesses to install botnet malware on devices in a smart home. Make botnet security a priority when building your own smart home or buying smart devices.
Botnets have been behind several of the most destructive cyberattacks in recent years. Here’s a closer look at a few of the most notorious botnets.
With over 10.5 million devices under its control at its height in 2008, the Conficker botnet is still one of the largest botnets ever created. A computer worm type of botnet, Conficker spread at unprecedented rates.
Having reached government networks across Europe, Conficker had already caused millions in damages and was poised to wreak havoc worldwide. But fortunately, the botnet was never used in a DDoS attack. It’s now believed to exist on around 500,000 computers around the world.
An encrypted P2P botnet derived from the ZeuS malware family, Gameover ZeuS was notoriously used to steal banking credentials from millions of victims. By the time it was dismantled, Gameover Zeus was believed to have caused losses of over $100 million.
In 2013, the Gameover ZeuS botnet was used to infect victims with CryptoLocker ransomware. The devastating ransomware attack extorted millions of dollars in bitcoin from victims before the Gameover ZeuS botnet was shut down in 2014 by Operation Tovar, an international task force which included the FBI and Europol.
Targeting Linux devices like routers and webcams, the Mirai botnet was discovered in 2016 and identified as responsible for several high-profile DDoS attacks. Mirai-infected machines scan the internet for IoT devices using default passwords and infect them when any are discovered.
After an initial wave of attacks in September 2016, Mirai’s source code was published online — letting other malware developers learn from it and create even better botnet malware.
The Mēris botnet blew up “botnet Twitter” in September 2021 after it slammed Russian internet company Yandex with a record-setting 21.8 million requests per second. The Mēris botnet comprises approximately 250,000 devices and also attacked web infrastructure provider Cloudflare earlier in the year.
Most of the bots in the Mēris botnet are network devices, like routers, made by Latvian manufacturer MikroTik. In previous attacks, the botnet creators would contact potential targets with the threat of attack if extortion demands were not met.
Since botnets don’t typically use significant processing power, it can be tricky to tell if your computer is part of a botnet. But there are a few other ways to figure out whether or not your computer has been roped into a botnet.
Sudden internet slowdowns or bandwidth spikes: Whether for sending spam emails or launching a DDoS attack, bandwidth is important for a botnet. Sudden bandwidth increases or drops in internet speed may indicate that a botnet is working in the background. This can also signal botnet malware in your smart home devices.
Unexplained changes to your system: A bot herder can alter your system files. If you notice any changes you can’t account for, someone else may have made them.
Inability to close processes: Botnet malware may prevent you from closing the programs it needs to carry out its mission. If there’s an app you can’t seem to close, it may be a botnet at work.
Inability to update your OS: Many botnets (and other types of malware) use OS and other software vulnerabilities to infect devices. Some botnet malware may prevent your OS from updating so that it can remain on your system.
Unknown processes in Task Manager: On Windows, the Task Manager shows you all the processes currently running on your computer. If you see anything here that you don’t recognize, look it up ASAP, as it might be botnet malware.
Your antivirus tool detects botnet malware: Many of the best free antivirus tools are excellent botnet scanners. They’ll scan for botnets and other threats, then remove the malware if any are found.
Get free botnet protection with Avast One, which detects malware, viruses, and other threats in real time to protect you against incoming infections. It’s a botnet checker and so much more — stay safe against all types of online threats, absolutely free.
Always update your software: Software updates include security patches against known weaknesses. Update your software whenever you can to keep botnet malware out.
Don’t open unexpected attachments: Only download and open attachments you’re expecting to receive from people you know. Even unexpected attachments from known sources can be phishing bait if your contact has been hacked.
Don’t click strange links: Phishing emails often contain links leading to malicious websites that can install malware via malvertising or drive-by downloads.
Steer clear of shady websites: Learn how to check websites for safety. If a website doesn’t seem trustworthy, close the window or tab.
Don’t use P2P download services: P2P downloads, such as torrents, may contain botnet malware. Get your media from legitimate and trustworthy sources instead.
Create new passwords when setting up new devices: If you’re installing a new router, webcam, or IoT device, change the login credentials immediately. This prevents botnet malware like Mirai from getting through using the default passwords.
Use a firewall: A good firewall will block connections from any already-installed botnet malware to its C&C server or other devices on a P2P botnet.
Use strong passwords: Some botnet malware will brute-force a password until it cracks. Create long and unique passwords or passphrases for much greater resistance to this type of attack.
Use two-factor authentication (2FA): 2FA prevents botnet malware from breaking into your devices and accounts if your password has been compromised.
Use antivirus software: A trustworthy antivirus tool will give you free botnet scanning and removal while protecting you against other types of malware as well.
Botnets overwhelmingly target devices with weak security — unprotected IoT devices and routers as well as computers and laptops with software vulnerabilities and easy-to-crack passwords. With a strong security tool on your side, you’ll be well protected against botnet malware and other online threats.
Avast One automatically detects and blocks malicious email attachments and websites — like the ones botnet creators use in phishing campaigns. And with 24/7 system monitoring, you’ll be protected ahead of time should any botnet malware target your devices. Get free botnet protection and removal today — and enjoy a suite of other security and privacy features — with Avast One.
Download free Avast One to protect your PC against botnets, malware, and other cybersecurity risks.
Download free Avast One to protect your Mac against botnets, malware, and other cybersecurity risks.
Install free Avast One to secure your iPhone against botnets, malware, and other online threats.
Install free Avast One to protect your Android phone against botnets, malware, and other cybersecurity risks.
Protect your Android phone against botnets and other threats with Avast One
Protect your iPhone against botnets and other threats with Avast One