Block hackers and protect your iPhone with Avast One
- Security
- Privacy
- Performance
Is your phone acting strangely? It could be a hacker. Unfortunately, phone hacking is a persistent threat, and it can affect the performance of your device and expose your personal data. Keep reading to learn the signs of phone hacking and what to do if you fall victim. Then, protect yourself with free mobile security software like Avast One.

Listen to the audio version
Phone hacking is the act of accessing a smartphone, its communications, or its data without consent. Phone hacking can range from stealing personal details to listening in on phone conversations. There are several ways someone can hack a phone, including using phishing attacks, tracking software, and unsecured Wi-Fi networks.

This Article Contains :
Phones are popular targets for hackers, because they contain so much personal information all in one place. Smartphones hold everything from email and phone contacts to banking and website login credentials. Hackers can sell this data on the dark web, use it to commit identity theft, or carry out a host of other cybercrimes.
Cybercriminals are always refining their methods — making their attacks increasingly difficult to spot. Attackers can even remotely deactivate your phone, so it’s essential that you stay one step ahead. Thankfully, there are clear phone hacking signs that can help you determine if you’ve been targeted.
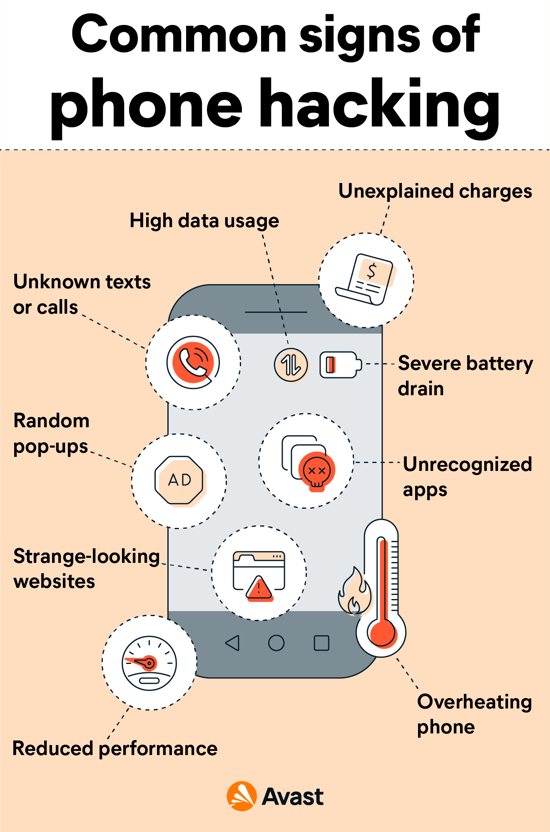
Here are the most common signs of phone hacking:
If you’re seeing a lot of pop-up ads, your phone could have an adware infection. If the problem persists, even when you have ad-blocking enabled, that could be a sign of potential hacking. Steer clear of these pop-ups, and don’t click or open them under any circumstances – it could make the problem worse.
Receiving communications from unrecognized numbers could indicate you’ve been the victim of a data breach. Don’t answer calls from unrecognized numbers, unless you’re expecting them or can verify their authenticity.
A hacked iPhone or Android phone can send text messages to all its contacts. If the phone of someone you know has been hacked, your number could be next. Check your call logs for any unusual activity, and if you see a number you don’t recognize, consider blocking the contact and reporting it as spam.
If your online activities haven’t changed much but your data usage has shot up, it could be a sign of a phone hacker. A malicious app running in the background can cause unusually high data usage. Review your apps and delete anything suspicious.
Are you charging your phone more often? Is your battery draining much more quickly than it used to? Your phone might simply be getting old, or you could have more than just a battery issue. Unwanted apps installed on your phone via hacking or other means can hijack your phone’s resources and drain your battery quickly.
Is your iPhone or Android getting hot and staying hot, even when you’re not using it? Like all devices, prolonged use — especially if you’re streaming or gaming for long periods of time — can cause your phone to get hot.
But if that’s not happening and your phone still feels unnaturally hot, malicious software might be causing it to overheat.
Is your phone dropping calls? Are you not receiving texts or are texts you’ve sent not getting through? Is your phone freezing, crashing, or unexpectedly rebooting all the time? The culprit may be malware or unwanted background apps draining your phone’s processing power.
If you’ve ruled out hackers, consider fixing crashing apps on Android.
A hacked iPhone or Android phone infected with malware can redirect you to unwanted, infected websites. If websites look odd to you, they might have undergone a redesign recently, or it might mean you’ve inadvertently ended up on an unsafe website.
If your phone bill is higher than usual, you could be incurring unexpected charges from unwanted apps spiking your data use. Fleeceware apps stuff your bill with excess charges, and if someone has remote access to your phone, they might take advantage of your subscriptions and other services.
If you have unwanted subscription fees on your phone bill, consider canceling those subscriptions, and delete infected apps immediately.
A telltale sign your phone is hacked is if you notice new and unfamiliar changes to the settings of your device. For instance, if you notice that your camera or microphone permissions have been altered, it could be due to hackers trying to monitor your actions. If you find that privacy and security settings have been changed, this is a major red flag that your phone has been compromised.
Strange apps that you didn't install shouldn’t end up on your phone. If you notice an app on your phone that you didn’t put there, a phone hacker might be responsible. Of course, some unnecessary apps come pre-installed on new phones (these are called bloatware). So if you don’t recognize an app, it doesn’t necessarily mean it’s malicious.
Everyone uses their phones differently. Sometimes phones with limited storage space or older phones show similar symptoms to a hacked device. So you don’t need to immediately assume you’ve been hacked.
But if you do notice strange apps that are hard to remove, see outrageous charges on your bill, or experience other problems that signal a malware infection, take immediate action. Check out our guide to removing viruses on Android or getting rid of malware on iPhones.
Sometimes it’s not easy to know you’ve been hacked. A mobile antivirus program like Avast One will automatically defend your phone from hackers. Avast One regularly scans your device for threats and detects malicious apps before you install them. Plus, it protects against malware-infected links and other online threats.
Phone hacking usually happens after a target or victim takes some kind of action, like clicking an infected link. Often, a phone hacker tricks people through a combination of social engineering techniques, technical trickery, and exploiting security vulnerabilities.
Here are some of the most common ways a phone can be hacked:
Phishing is a targeted cyberattack that lures victims into clicking a malicious link, downloading a dangerous attachment, or sending personal or other sensitive information. The aim is to obtain a victim’s private data.
Phishing attacks are usually carried out over email or text messages. The attacker may cast a wide net or bait specific groups or individuals in what’s known as spear phishing. All hackers need is a convincing email or iPhone message for the hack to take place. Depending on the private data they catch, hackers can gain access to various accounts and devices, including your phone.
Tracking software monitors and records device activity. Although web tracking can be legitimate, sometimes it’s really spyware that’s used by hackers (or even family members) to record and steal private data. The use of Pegasus spyware against politicians, journalists, and activists is a particularly potent recent example.
Hackers can also use keyloggers and other tracking software to capture your phone’s keystrokes and record what you type, such as search queries, login credentials, passwords, credit card details, and other sensitive information.
Hackers can easily break into unsecured wireless networks and steal personal information and spy on private communications. Use a VPN to browse safely on public Wi-Fi and ensure an encrypted, private connection.
Hackers can break into Bluetooth devices, too — so avoid pairing your phone to an unknown Bluetooth connection. Learn how to tell if your Bluetooth is hacked and read up on the most secure type of Wi-Fi connections.
A SIM swap attack happens when criminals fraudulently request a new SIM card from your mobile service provider using personal data they’ve phished out of you or that you’ve made public on social media. A SIM swap attack can give a hacker full access to your phone number, meaning they’ll receive all your texts and calls.
Typically, the main goal of a SIM swap attack is to gain malicious access to your bank or other accounts using 2FA texts. As well as following privacy and security best practices to protect your private information, you can also guard against SIM swap attacks by setting a tough security question with your service provider.
It’s rare, but some counterfeit USB cables are rigged to send data wirelessly to a hacker’s computer, and fakes can be practically indistinguishable from real Apple iPhone cables. Make sure you buy only legitimate phone accessories from official stores, and avoid plugging in cables — or any other hardware — belonging to anyone you don’t trust.
Trojan horse malware looks like a legitimate app, but in reality it’s full of malicious code designed to harm your device or steal information. Apple verifies apps on their App Store quite rigorously, but trojans are far more common on Android, so avoid installing any apps you’re unsure of, and make sure you install one of the best antivirus software tools to catch anything that slips through.
Cryptominers use your device’s processing power to help generate cryptocurrency. When done without your permission, cryptomining is a form of hacking called cryptojacking. But even “legit” cryptomining apps can be so aggressive with your phone that it overheats and stops working. And it can compromise your device security in other ways.
Android phones are more common targets for phone hacking than iPhones, mainly because the Android operating system is used by more phones and more people — so there’s a bigger pool of targets. But phone hackers are increasingly targeting iPhones, so iPhone users are still at risk.
In other words, just like how Macbooks can get viruses, iPhones can get hacked. But Android devices are generally easier to hack, because of the more open nature of the Android operating system.
The iPhone’s iOS operating system is a closed development environment. Apple does not give out its source code to app or system developers, and its devices can’t be modified (unless you jailbreak them). Because it’s harder for software engineers to get apps approved on the App Store and installed onto iPhones, it’s more difficult for hackers to meddle with iOS devices.
By contrast, Android is an open-source operating system created by Google. Android shares its source code with app and system developers. That makes it easier for developers to create plugins, enhancements, and other modifications. And while this encourages innovation, it also makes Android devices generally easier to hack.
Regardless of which phone you use, always keep it updated to fix OS bugs and patch exploitable security vulnerabilities. And only download apps from trusted sources like Google Play or Apple’s App Store.
If your phone has been hacked, act quickly to limit the damage. There are simple steps you can take to minimize the danger and fix your hacked phone.
Here’s what to do if someone hacks your phone:
First, remove the offending software. Review all your apps and check for anything unfamiliar. Hackers can install malware that seems like a harmless background app. Verify the legitimacy of any apps you don’t recognize and delete any suspicious apps.
A strong malware scanner and removal tool will scan your phone to identify and remove anything malicious. This step is essential, because if you miss remnants of an attack, the issue can arise again.
A factory reset can remove most malware — although you’ll lose all the data stored on your phone. Before resetting your phone, make a backup of all your contacts, photos, notes, etc.
When it comes to what to do if your phone is hacked, resetting the device should be your very last resort. You might lose important files, so tread carefully.
Resetting your iPhone will remove all your settings and data, but if you need to fix a hacked iPhone, this will clean up your device. Backup everything before restoring your iPhone so you don’t lose important files.
Here’s how to factory reset your iPhone:
Connect your phone to your computer via USB, start iTunes, and click the iPhone icon.
Click Restore iPhone and follow the on-screen instructions.
If you need to start from a clean slate, you can restore your Android to its factory settings. This will delete everything, so make sure your critical files are backed up.
Here’s how to restore your Android phone to factory settings:
Go to Settings and tap General management.
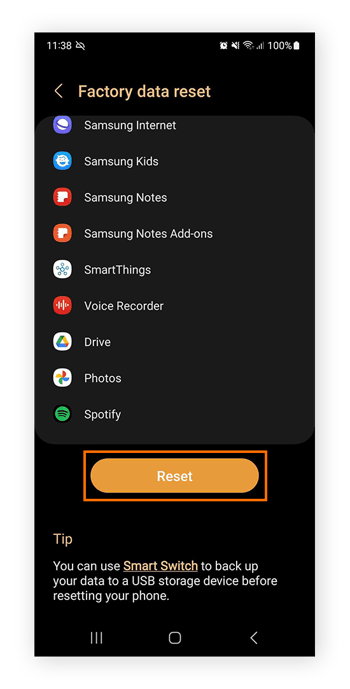
Tap Reset then Factory data reset.
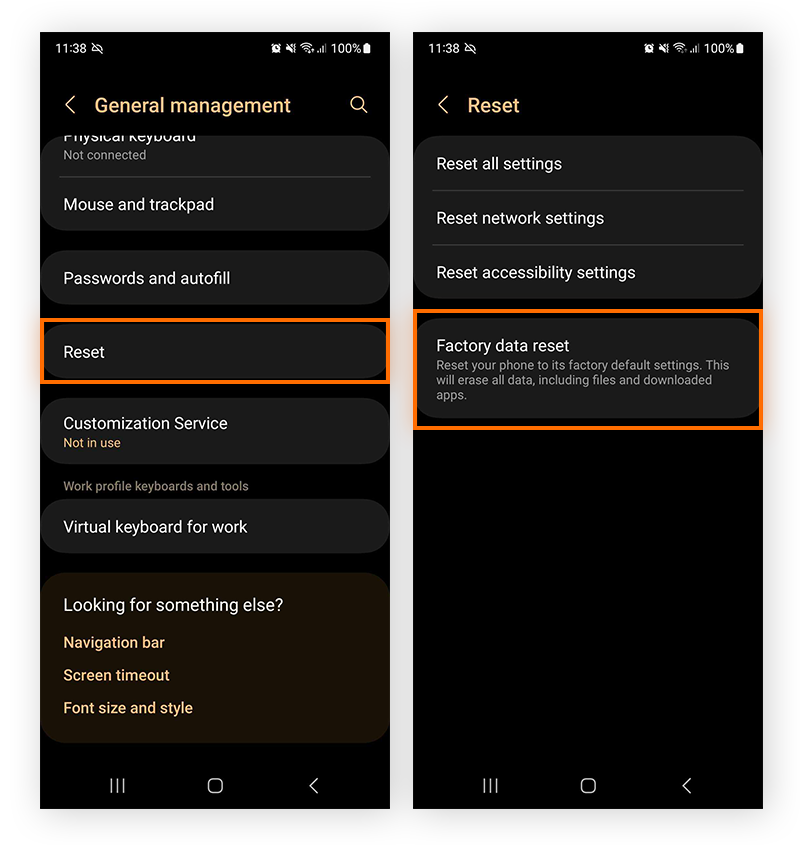
Confirm by tapping the Reset button.
If you’ve been hacked, change your old passwords and your phone’s access code. And change all your passwords for the accounts connected to your phone. This includes login credentials for your social media accounts, online banking portals, cloud sharing services, and anything else connected to your phone. Always create strong passwords to prevent future security breaches.
 If your phone is hacked, delete unusual apps, scan for malware, restore your device, and reset your passwords.
If your phone is hacked, delete unusual apps, scan for malware, restore your device, and reset your passwords.
It’s possible your hacked phone was used to send phishing emails or other scam or spam messages to people you know, so it’s important to let your contacts know if you’ve been hacked. Warn them not to click links or otherwise interact with any strange messages — otherwise they may become the next victim.
A hacked phone may be diverting texts and calls to a hacker’s device, so contact your mobile service provider so that they can freeze any unauthorized activity, restore your phone number, and resecure your account by adding a PIN or security question.
Fixing your phone and safeguarding your personal data after a breach is no fun. That’s why it’s important to ensure it never happens in the first place. With regular maintenance and good digital hygiene, you can strengthen your protection against phone hacking while also securing your personal data and devices.
Here are the best security practices to prevent phone hacks:
Use strong passwords: Simple passwords are easy to guess. Create long, unique, hard-to-guess passwords or passphrases to prevent them from being cracked. Don’t reuse passwords for different accounts, and get one of the best password managers to keep track of them all. Good password practice is one of the best ways to protect your phone from hackers.
Use two-factor authentication and biometrics: With two-factor authentication (2FA), hackers need more than just your password to access your accounts. And although governmental biometrics usage is dubious, biometric technology (like facial recognition) can help keep hackers away. Make sure you do your research first.
Clear cookies and browsing history: The digital data trail you leave behind can be used to create a profile of you and your habits. Delete your browser cookies to keep your personal information private.
Install updates: Software is constantly evolving. Updates are a way for developers to fix problems and patch security issues. Always install software updates to make sure you have the most up-to-date version of your programs.
Use antivirus software: Even if you’re hyper-vigilant, hacks and malware can slip through. Regularly running strong antivirus software will not only scan and remove any threats on your phone, it’ll also give you real-time protection by detecting threats as they emerge.
If you have an Android phone, get Avast Mobile Security for Android. And if you have an iPhone, install Mobile Security for iOS.
Use a VPN on public Wi-Fi: Unsecured, public Wi-Fi networks are easy targets for hackers. You need a VPN to encrypt your connection and keep you hidden from snoops.
Don’t jailbreak: Jailbreaking (also called rooting) refers to altering core software to avoid restrictions set up by developers or manufacturers. Jailbreaking works by altering your phone’s operating system. While it lets you make root modifications to your phone, it also makes you more vulnerable. Without the built-in security of the original operating system, hackers have a better chance to hack your phone and infect it with malware.
Many SIM cards have a default password of “1234,” so one way to prevent anyone else accessing your texts or calls is to lock your SIM card by changing your PIN. But beware — if you get locked out of your own SIM because you’ve forgotten the PIN, it may be impossible to recover access.
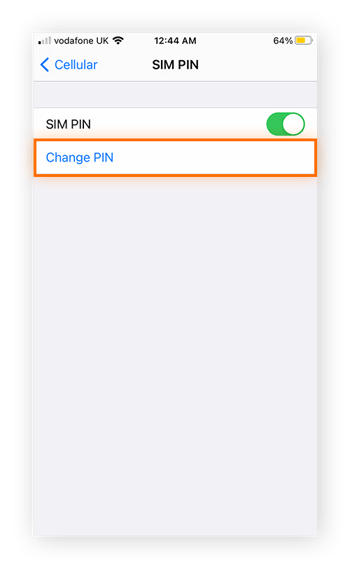
Here’s how to change the SIM PIN on an iPhone:
Tap Settings, then Cellular followed by SIM PIN.
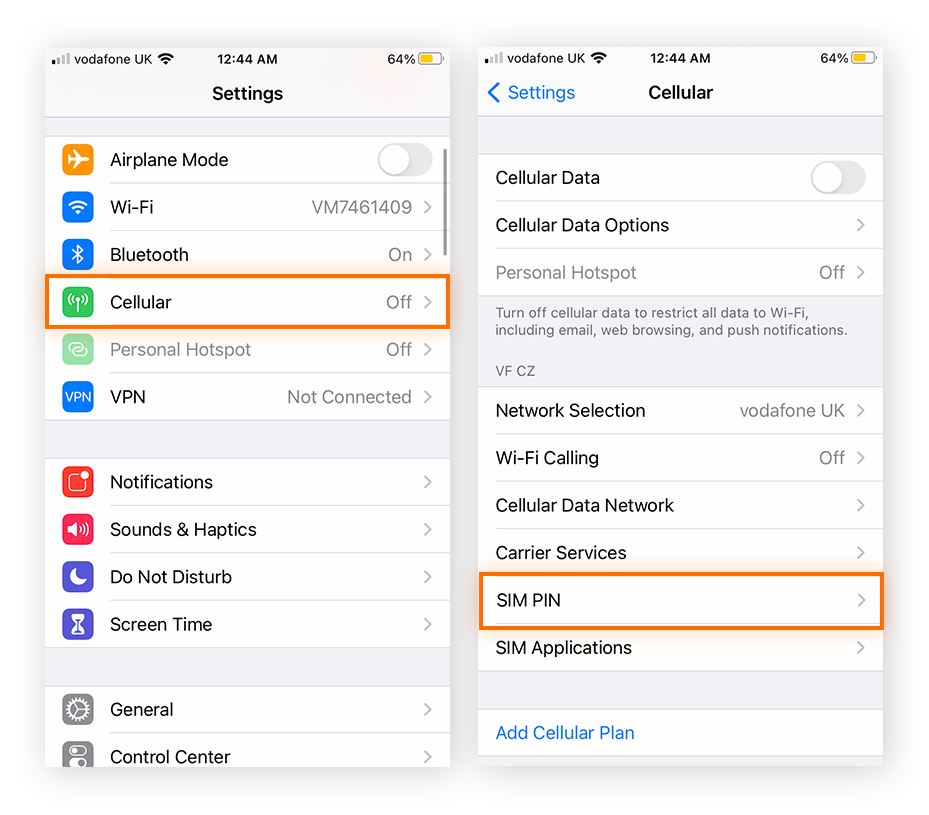
Make sure SIM PIN is toggled on (green), then tap Change PIN. Enter your new PIN and don’t forget it.
Cutting off internet and Bluetooth connectivity “air gaps” your device, meaning hackers can’t remotely plant malware on (or retrieve information from) your phone. As well as preventing hacking in the first place, if your device is already compromised, turning off Wi-Fi and Bluetooth helps you run an antivirus scan to make sure that nothing harmful is lingering on your phone.
The more you minimize the amount of identifying information on your phone, the less vulnerable you are to hacking attempts. Remove any pictures, notes, files, or apps that may reference sensitive data such as:
Passport/ID card scans
Birthday or place of birth
Full names of your parents or siblings
Birthdays of your parents or siblings
Your full name or maiden name
Details of recent trips you’ve taken
Photos of your bank cards
If you download apps from third-party sources, there's a high risk of downloading trojan malware. But official online stores such as Google Play or Apple's App Store have robust systems for vetting apps, helping to ensure user safety and security when installing apps.
If you receive any suspicious-looking emails or text messages containing questionable links or attachments, don’t click on them. They may contain spyware that lets a hacker snoop on your device, or direct you to a fake website designed to steal your personal information.
From photos to finances, our personal lives are inseparable from our phones. Practicing good digital hygiene is essential to avoid hackers. Don’t risk your phone getting hacked and your personal data being compromised.
Avast One will detect and alert you in the event of a malware attack. Plus, it will automatically scan your phone for threats, protect your browsing with a web shield, and keep you safe from other online scams. Turn your phone into a fortress with Avast.
Turning off a phone stops most hacking attempts — if there’s no internet connection, code usually can’t execute and nothing can happen. However, when powered down, the newest iPhone models enter a low-power state instead of turning off completely, allowing the use of services like Find My iPhone. There’s a chance this feature could be exploited by hackers in the future.
It’s impossible to get hacked by simply answering a phone call made through your network service provider. But that doesn’t mean a phone call can’t be exploited to compromise your security via a social engineering attack.
You can get hacked through WhatsApp if you click a malicious link or attachment. And even accepting a WhatsApp call can theoretically plant malware on your phone, so be wary of incoming calls or messages from numbers you don’t know. And keep WhatsApp updated to benefit from the latest security patches.
If your device has been compromised, it’s possible for someone to hack into your phone camera and spy on you in real-time. This can be done remotely over a Wi-Fi network, and it’s just one of many reasons why you should use a VPN whenever you use unsecured public Wi-Fi.
Fake or malicious websites can hack your phone through sophisticated drive-by downloads that can launch an attack without any user interaction such as clicking a link or downloading a file. Even legitimate websites can be abused by hackers to infect your device via malvertising pop-ups and banners.
Install free Avast One to block hackers, protect your data, and get real-time protection for your phone.
Install free Avast One to block hackers, protect your data, and get real-time protection for your phone.
Install free Avast One to block hackers, protect your data, and get real-time protection for your phone.
Install free Avast One to block hackers, protect your data, and get real-time protection for your phone.
Block hackers and protect your iPhone with Avast One
Block hackers and protect your phone with Avast One